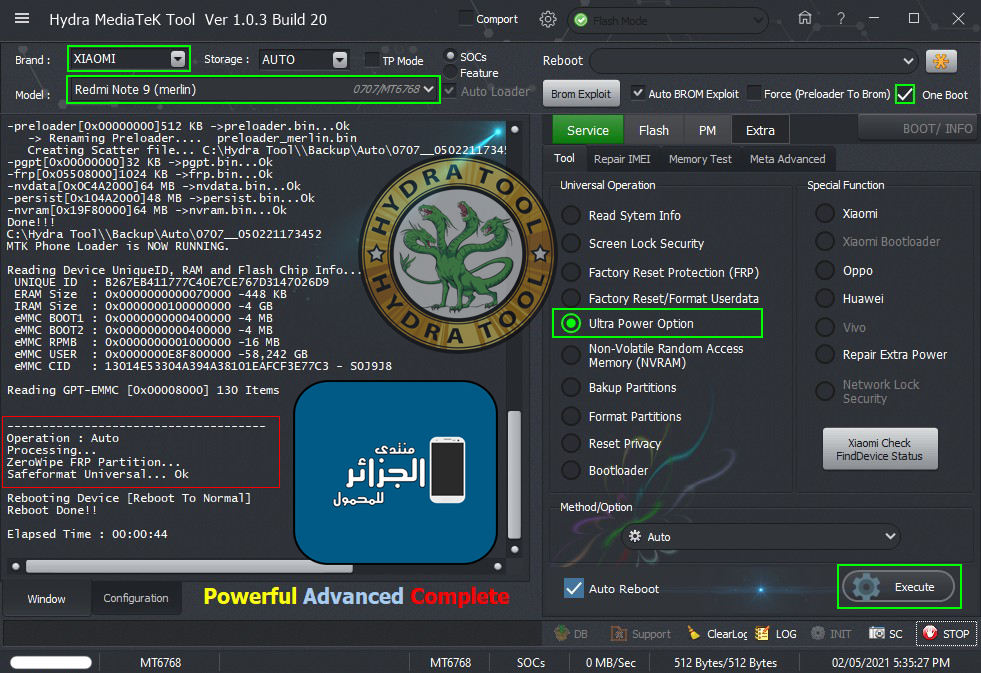
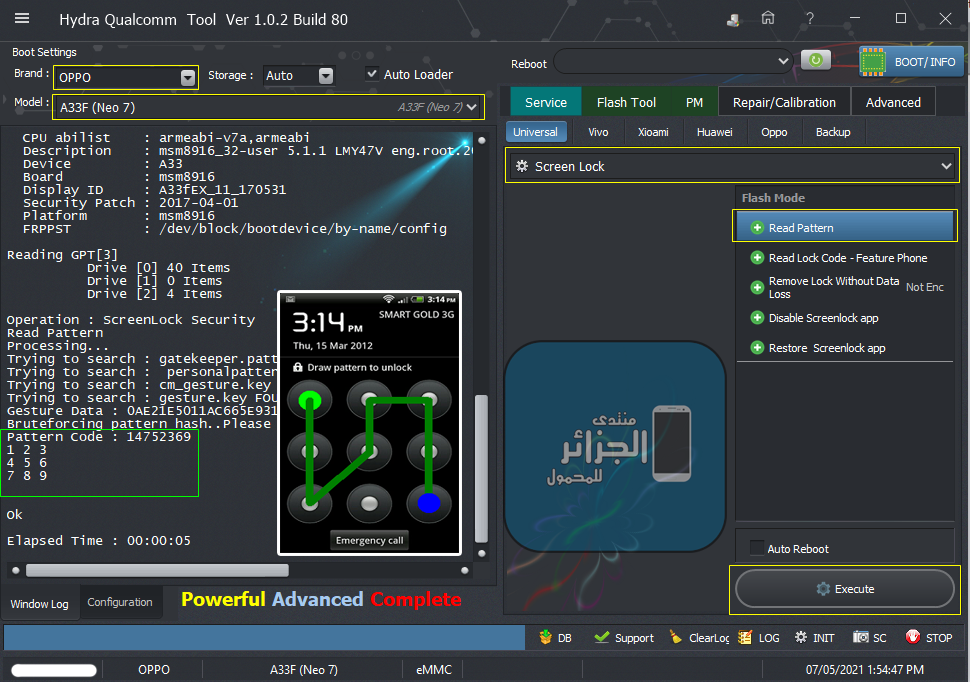
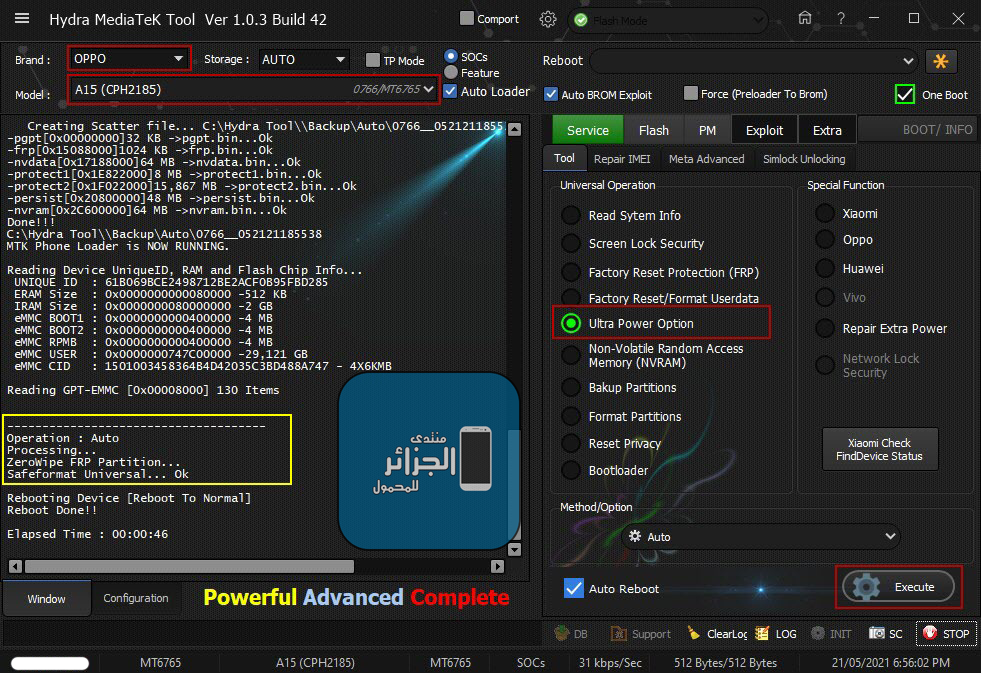
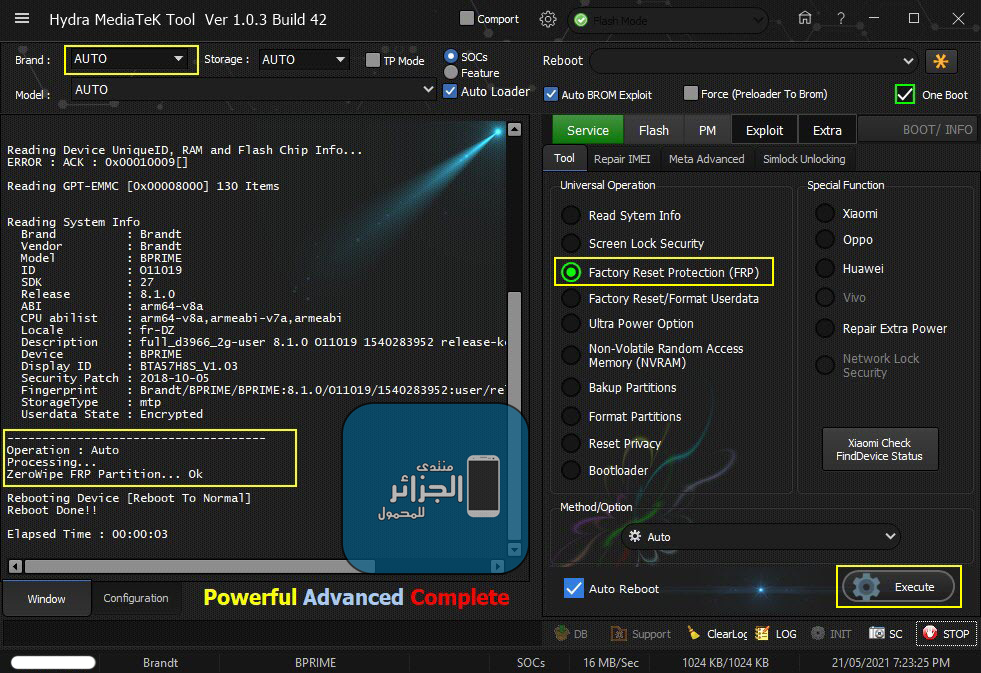
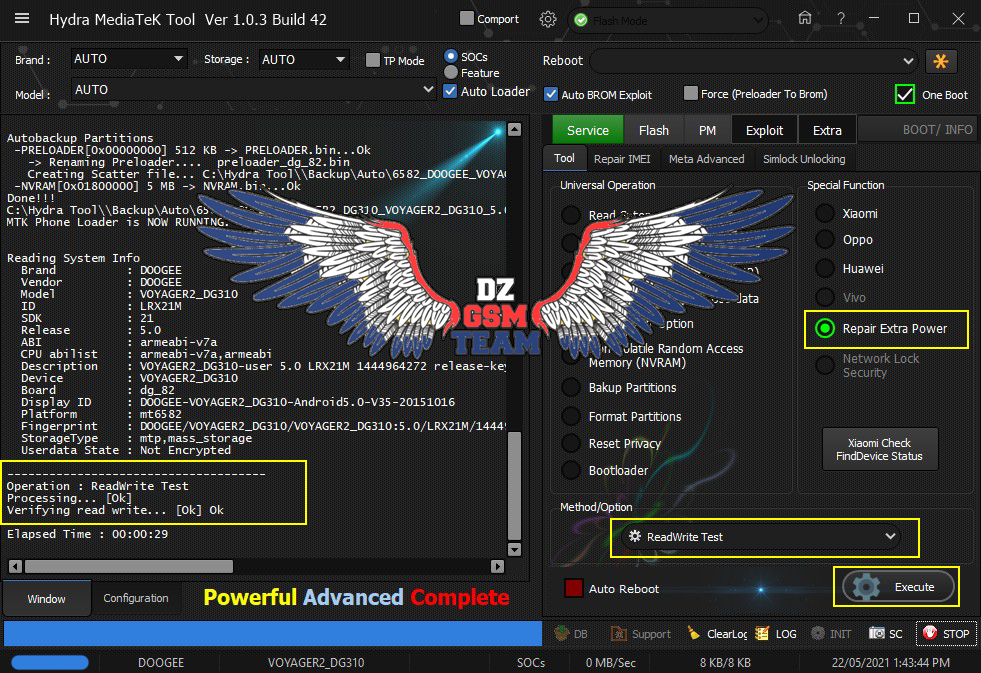
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
Xiaomi Redmi Note 8 Flash Fastboot Done
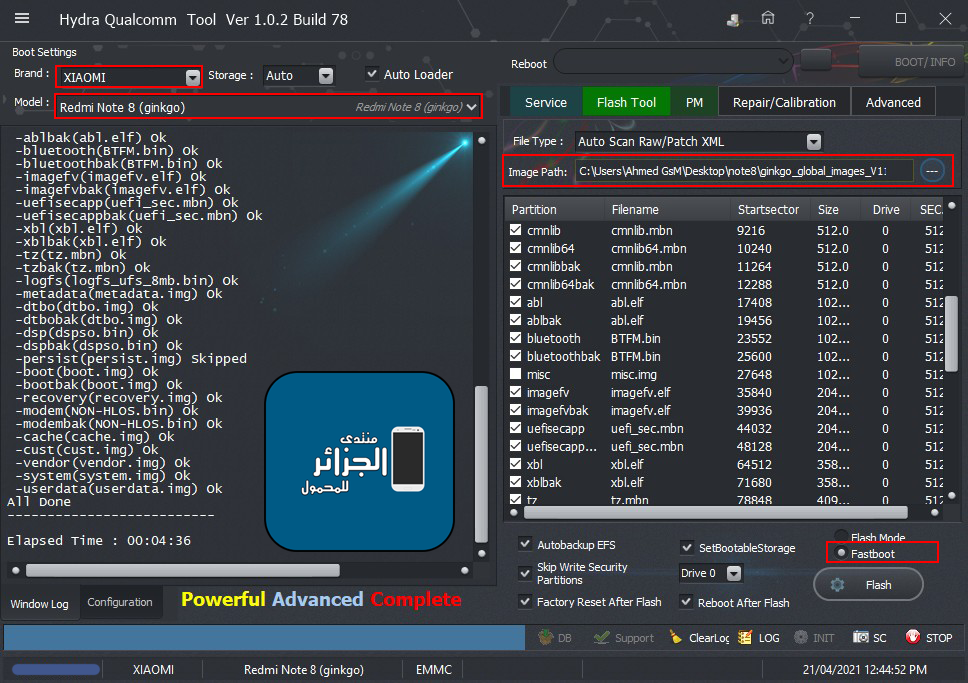
Xiaomi Redmi Note 8 Flash Fastboot Done

كود:
[B][FONT=Arial Black][SIZE=2]Searching Device By Fastboot
Device Found...
Reading Information...getvar:version FAILED (remote: GetVar Variable Not found)
Product : ginkgo
version : getvar:version FAILED (remote: GetVar Variable Not found)
Secure : yes
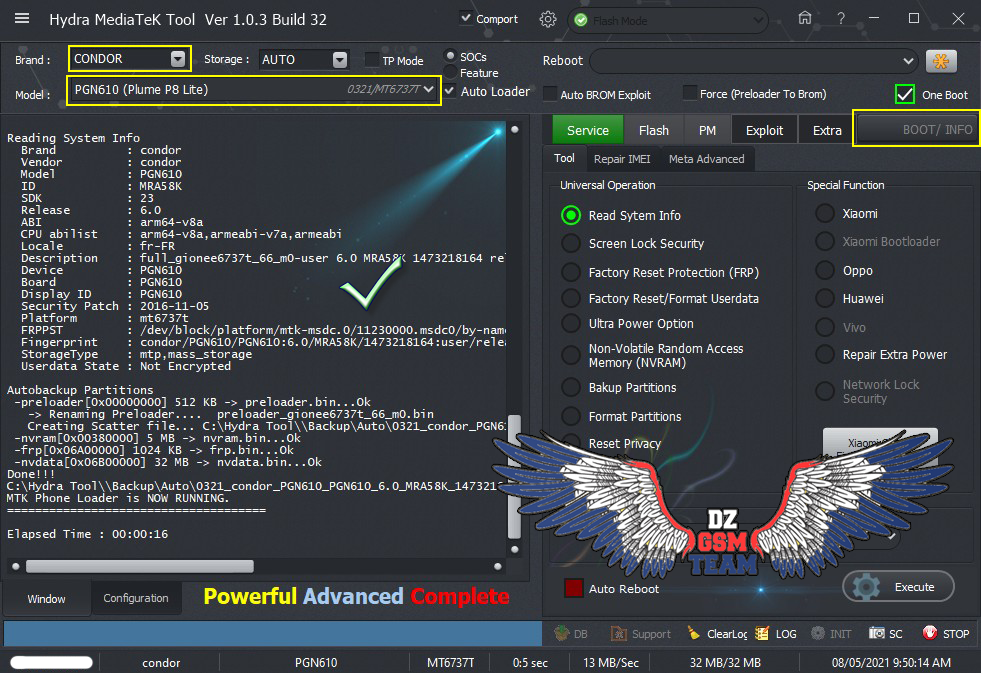
Device Info:
Verity mode: true
Device unlocked: true
Device critical unlocked: true
Charger screen enabled: true
--------------------------
Fastboot Flashing...
-qupfw(qupv3fw.elf) Ok
-qupfwbak(qupv3fw.elf) Ok
-vbmeta(vbmeta.img) Ok
-vbmetabak(vbmeta.img) Ok
-xbl_config(xbl_config.elf) Ok
-xbl_configbak(xbl_config.elf) Ok
-devcfg(devcfg.mbn) Ok
-devcfgbak(devcfg.mbn) Ok
-storsec(storsec.mbn) Ok
-rpm(rpm.mbn) Ok
-rpmbak(rpm.mbn) Ok
-hyp(hyp.mbn) Ok
-hypbak(hyp.mbn) Ok
-keymaster(km4.mbn) Ok
-keymasterbak(km4.mbn) Ok
-cmnlib(cmnlib.mbn) Ok
-cmnlib64(cmnlib64.mbn) Ok
-cmnlibbak(cmnlib.mbn) Ok
-cmnlib64bak(cmnlib64.mbn) Ok
-abl(abl.elf) Ok
-ablbak(abl.elf) Ok
-bluetooth(BTFM.bin) Ok
-bluetoothbak(BTFM.bin) Ok
-imagefv(imagefv.elf) Ok
-imagefvbak(imagefv.elf) Ok
-uefisecapp(uefi_sec.mbn) Ok
-uefisecappbak(uefi_sec.mbn) Ok
-xbl(xbl.elf) Ok
-xblbak(xbl.elf) Ok
-tz(tz.mbn) Ok
-tzbak(tz.mbn) Ok
-logfs(logfs_ufs_8mb.bin) Ok
-metadata(metadata.img) Ok
-dtbo(dtbo.img) Ok
-dtbobak(dtbo.img) Ok
-dsp(dspso.bin) Ok
-dspbak(dspso.bin) Ok
-persist(persist.img) Skipped
-boot(boot.img) Ok
-bootbak(boot.img) Ok
-recovery(recovery.img) Ok
-modem(NON-HLOS.bin) Ok
-modembak(NON-HLOS.bin) Ok
-cache(cache.img) Ok
-cust(cust.img) Ok
-vendor(vendor.img) Ok
-system(system.img) Ok
-userdata(userdata.img) Ok
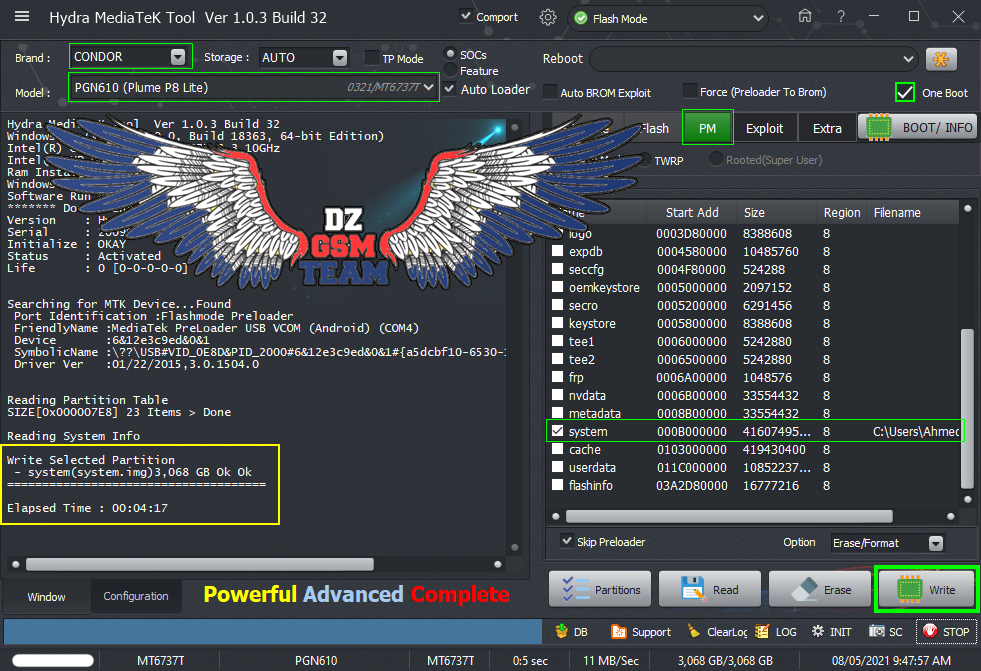
All Done
--------------------------
Elapsed Time : 00:04:36
[/SIZE][/FONT][/B]