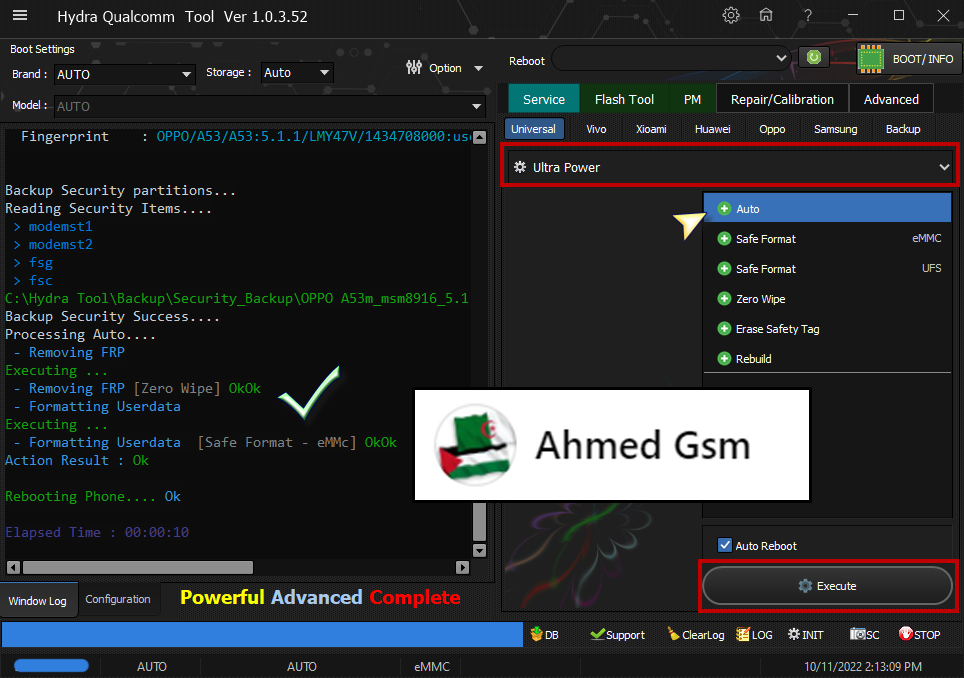
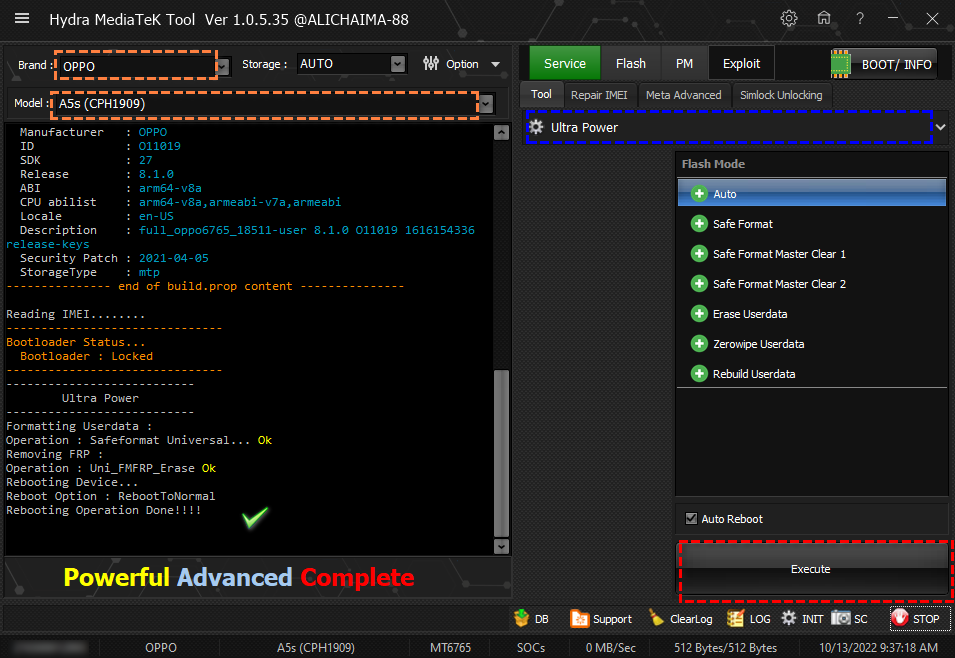
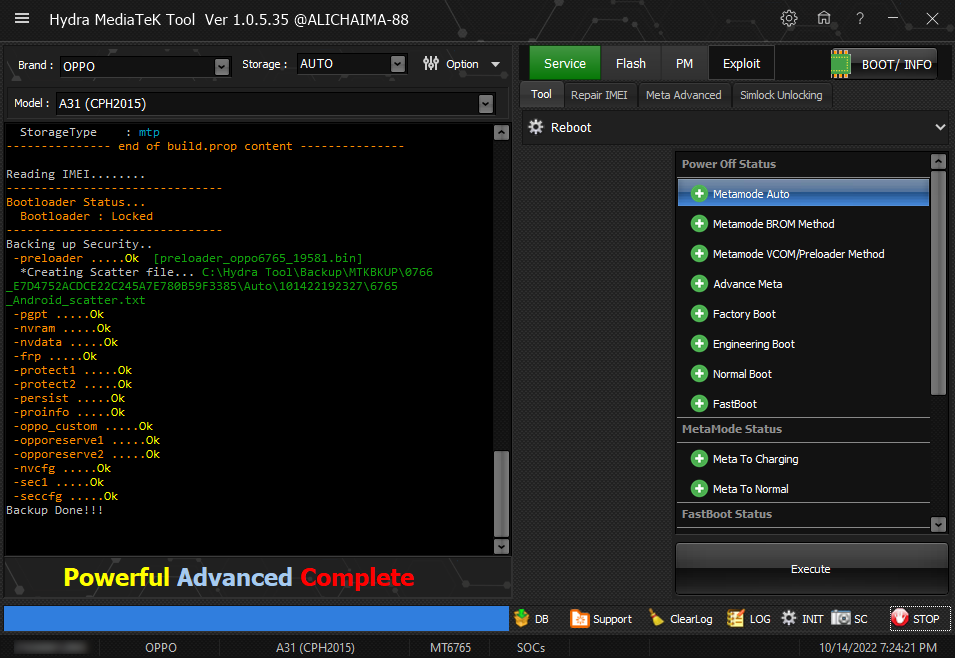
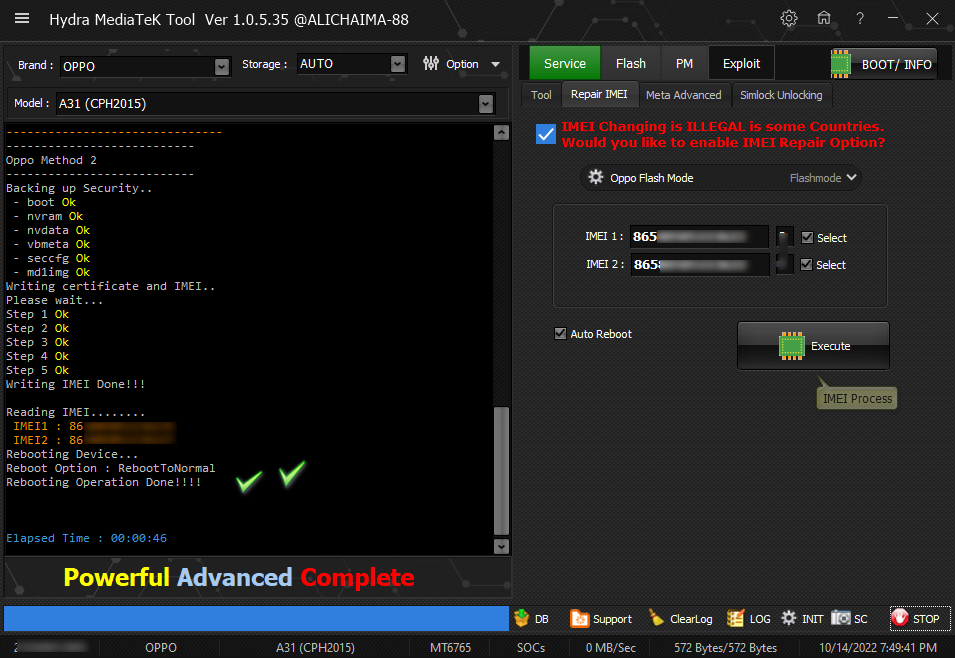
رد: تجارب الأعضاء الناجحة فى تصليح و تفليش و فك شفرات الأجهزة على Hydra Dongle
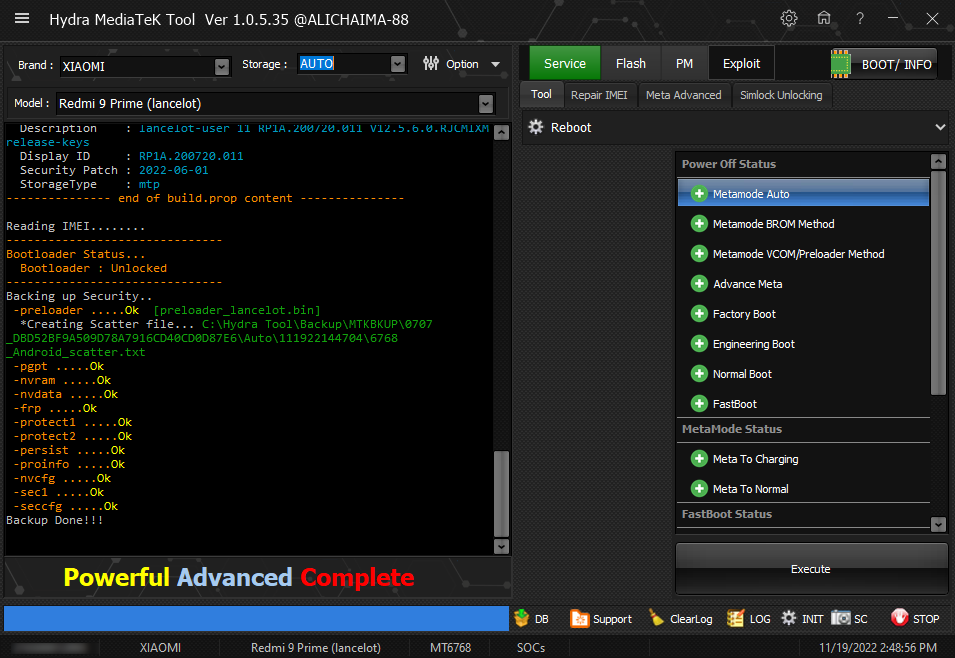
Xiaomi Redmi 9 (lancelot) Removing FRP By Hydra Tool
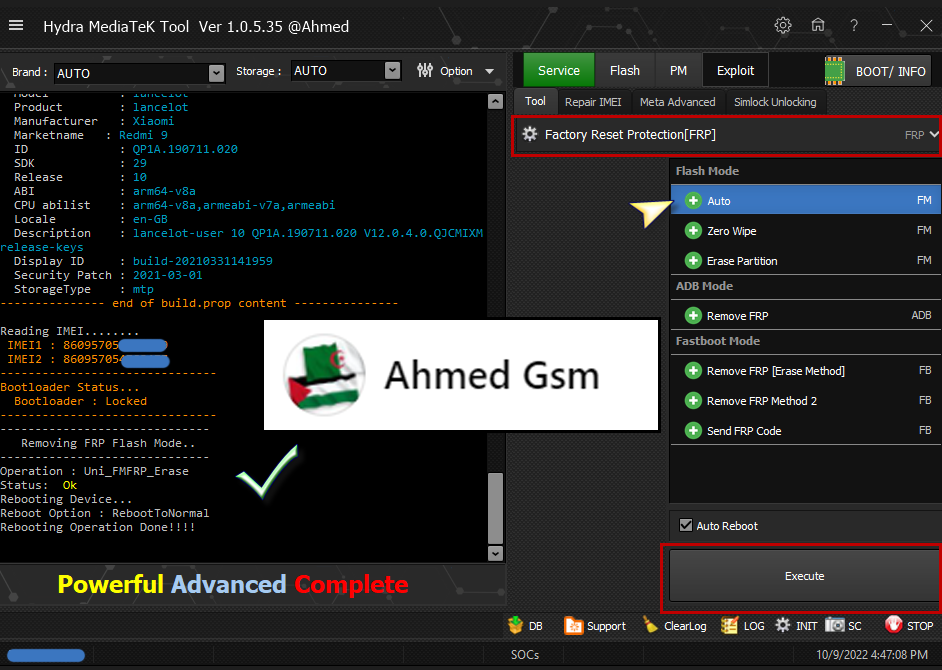
Xiaomi Redmi 9 (lancelot) Removing FRP By Hydra Tool

كود:
[B][FONT=Arial Black]Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM3)
Device :5&df74106&0&2
SymbolicName ??\USB#VID_0E8D&PID_0003#5&df74106&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2016,3.2
Trying to Open Port [COM3] Ok
Handshaking...Ok
HwCode : 0707 {MT6768}
Hwver : 0000
Target config : E7
SBC : 01 (True)
SLA : 02 (True)
DAA : 04 (True)
SWJTAG : 06 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Device Connection : BROM
HW Subcode: 8A00
HW Ver : CA00
SW Ver : 0000
ME_ID : 476380D5F08011B4B3066C5EE4418456
SOC_ID : E17B052FB7305F13D21AF5587CD401852668A4D33BBA27F3F733AC652D5E5E21
Device not yet filterd...
Executing LibUSB Filter..
Device Now Filtered...Restarting Device Port..
Trying to Open Port [COM3] Ok
Handshaking...
Device Connection : BROM
Exploiting Device...
Handshaking...Ok
Dumping Preloader from Bootrom..
Seeking preloader address..Found @ 0x00200BC4
Starting to dump...
Prel Size : 0x000436D0
Successfully dump preloader.. [C:\Hydra Tool\Boot\PreloaderDump\preloader_lancelot.bin]
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
Device Connection : BROM
Download Agent...
DA :MTK_AllInOne_DA_5.2152.bin
Patching da2 ... Ok
Uploading data
Successfully uploaded stage 1, jumping ..
Jumping to 0x00200000
Successfully received DA sync
CONNECTION_AGENT : brom
DRAM config needed for : 150100444436384D
Sending emi data..
DRAM setup passed.
Sending emi data succeeded.
Uploading stage 2...
Upload data was accepted. Jumping to stage 2...
Successfully uploaded stage 2
ERAM Size: 0x0000000000070000-448 KB
IRAM Size: 0x0000000100000000-4 GB
EMMC Boot1 Size: 0x0000000000400000-4 MB
EMMC Boot2 Size: 0x0000000000400000-4 MB
EMMC RPMB Size : 0x0000000000400000-4 MB
EMMC USER Size : 0x0000000747C00000-29.121 GB
EMMC CID : 150100444436384D420991F9F4FA67D5 - DD68MB
HW-CODE : 0x707
HWSUB-CODE : 0x8A00
HW-VERSION : 0xCA00
SW-VERSION : 0x0
CHIP-EVOLUTION : 0x1
DA-VERSION : 1.0
Speed : high-speed
Upload data was accepted. Jumping to stage 2...
DA Extensions successfully added
Reading Partition Table ..
Partition Count : 50
--------------- Reading build.prop content ---------------
Brand : Redmi
Vendor : Xiaomi
Model : lancelot
Product : lancelot
Manufacturer : Xiaomi
Marketname : Redmi 9
ID : QP1A.190711.020
SDK : 29
Release : 10
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : lancelot-user 10 QP1A.190711.020 V12.0.4.0.QJCMIXM release-keys
Display ID : build-20210331141959
Security Patch : 2021-03-01
StorageType : mtp
--------------- end of build.prop content ---------------
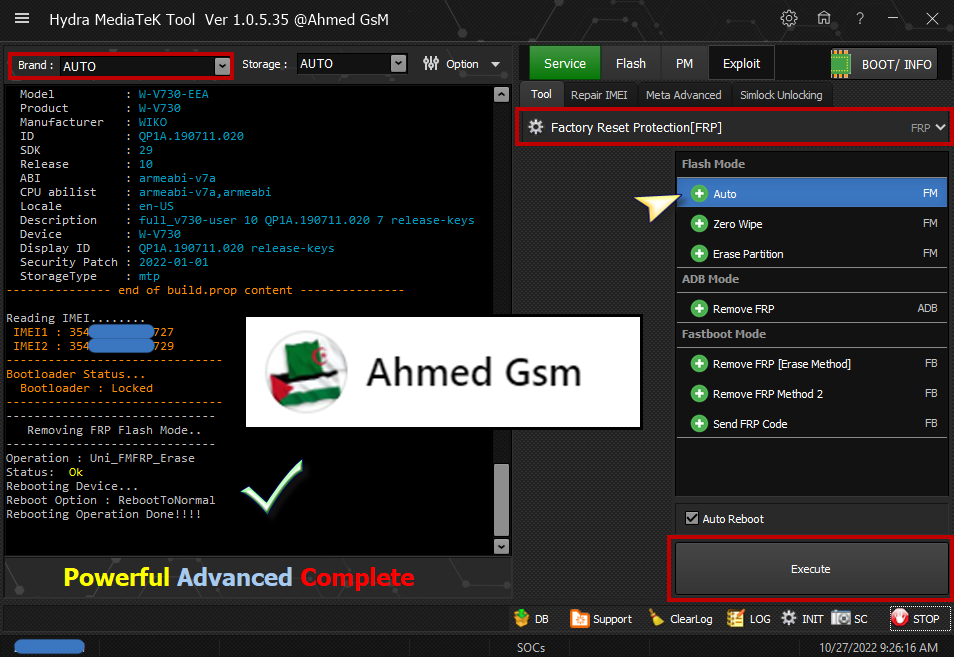
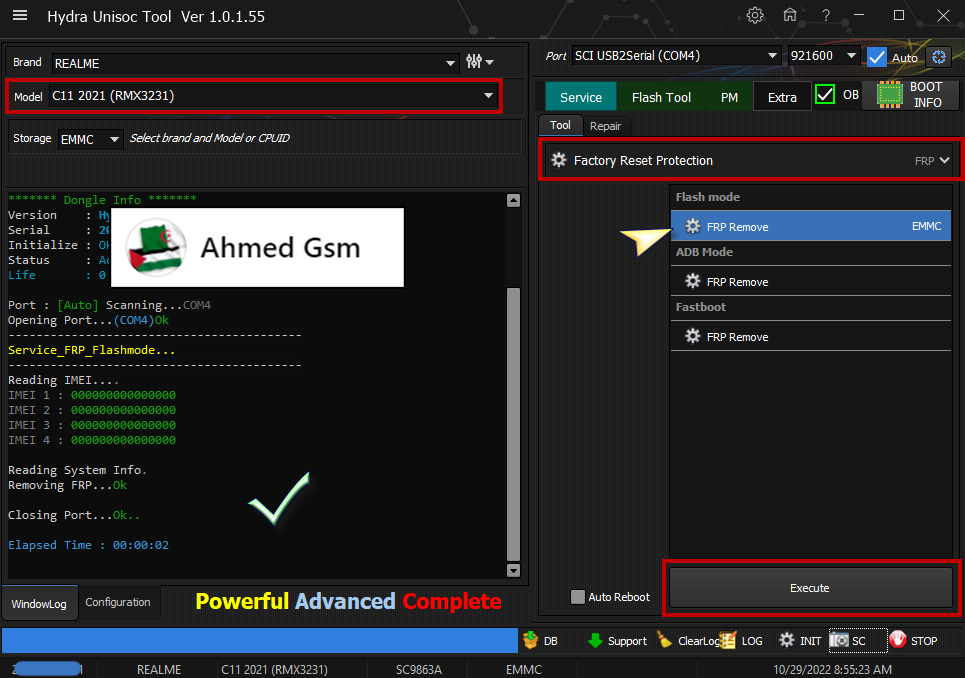
Reading IMEI........
IMEI1 : 860957054XXXXXX
IMEI2 : 860957054XXXXXX
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
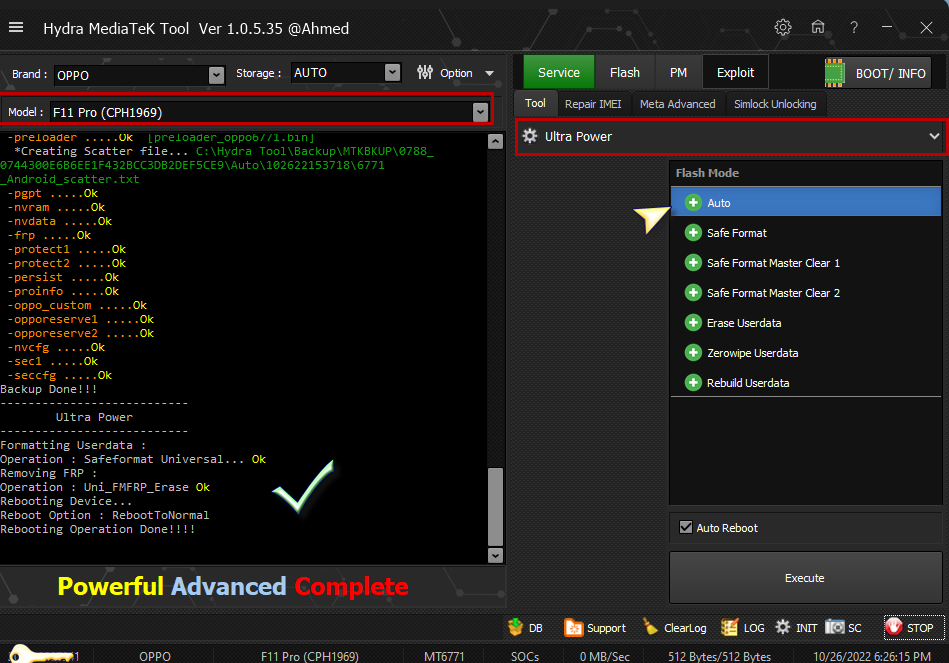
Backing up Security..
-preloader .....Ok [preloader_lancelot.bin]
*Creating Scatter file... C:\Hydra Tool\Backup\MTKBKUP\0707_476380D5F08011B4B3066C5EE4418456\Auto\100922161502\6768_Android_scatter.txt
-pgpt .....Ok
-nvram .....Ok
-nvdata .....Ok
-frp .....Ok
-protect1 .....Ok
-protect2 .....Ok
-persist .....Ok
-proinfo .....Ok
-nvcfg .....Ok
-sec1 .....Ok
-seccfg .....Ok
Backup Done!!!
Reading Partition Table ..
ERAM Size: 0x0000000000070000-448 KB
IRAM Size: 0x0000000100000000-4 GB
EMMC Boot1 Size: 0x0000000000400000-4 MB
EMMC Boot2 Size: 0x0000000000400000-4 MB
EMMC RPMB Size : 0x0000000000400000-4 MB
EMMC USER Size : 0x0000000747C00000-29.121 GB
EMMC CID : 150100444436384D420991F9F4FA67D5 - DD68MB
HW-CODE : 0x707
HWSUB-CODE : 0x8A00
HW-VERSION : 0xCA00
SW-VERSION : 0x0
CHIP-EVOLUTION : 0x1
DA-VERSION : 1.0
Speed : high-speed
Partition Count : 50
--------------- Reading build.prop content ---------------
Brand : Redmi
Vendor : Xiaomi
Model : lancelot
Product : lancelot
Manufacturer : Xiaomi
Marketname : Redmi 9
ID : QP1A.190711.020
SDK : 29
Release : 10
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : lancelot-user 10 QP1A.190711.020 V12.0.4.0.QJCMIXM release-keys
Display ID : build-20210331141959
Security Patch : 2021-03-01
StorageType : mtp
--------------- end of build.prop content ---------------
Reading IMEI........
IMEI1 : 860957054XXXXXX
IMEI2 : 860957054XXXXXX
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
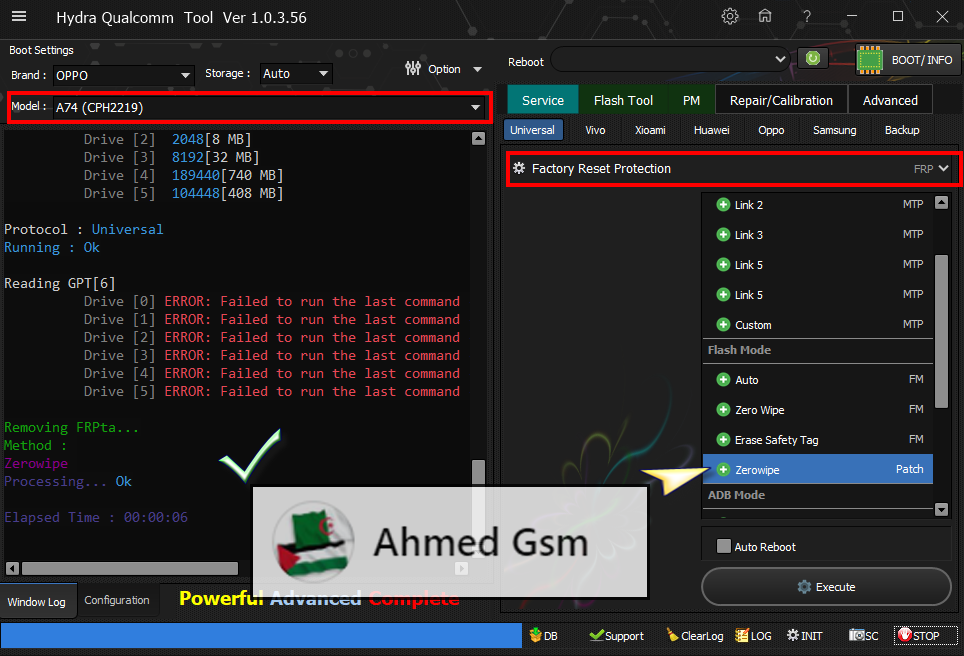
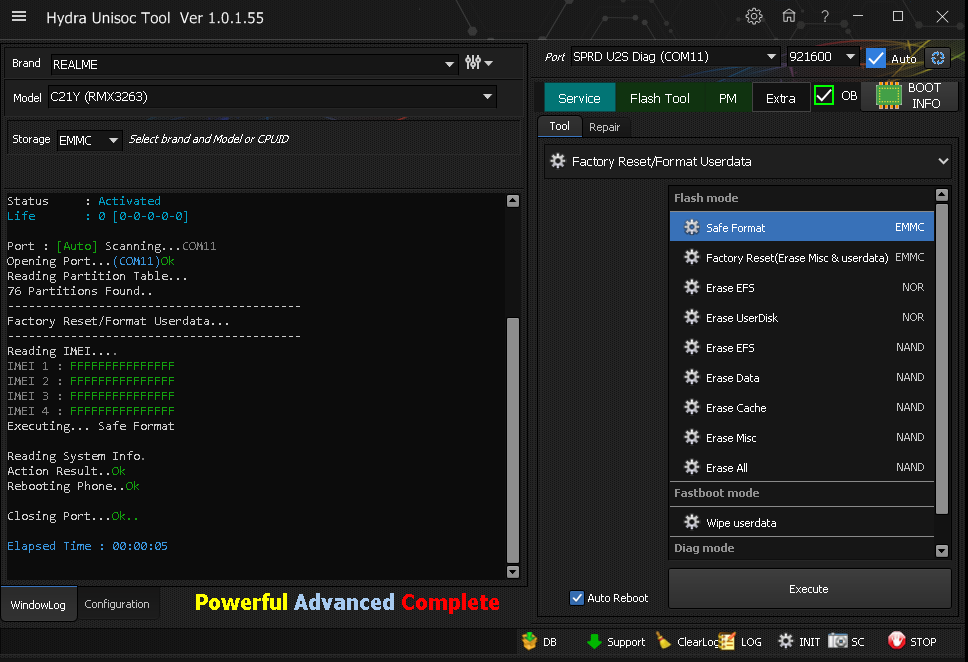
------------------------------
Removing FRP Flash Mode..
------------------------------
Operation : Uni_FMFRP_Erase
Status: Ok
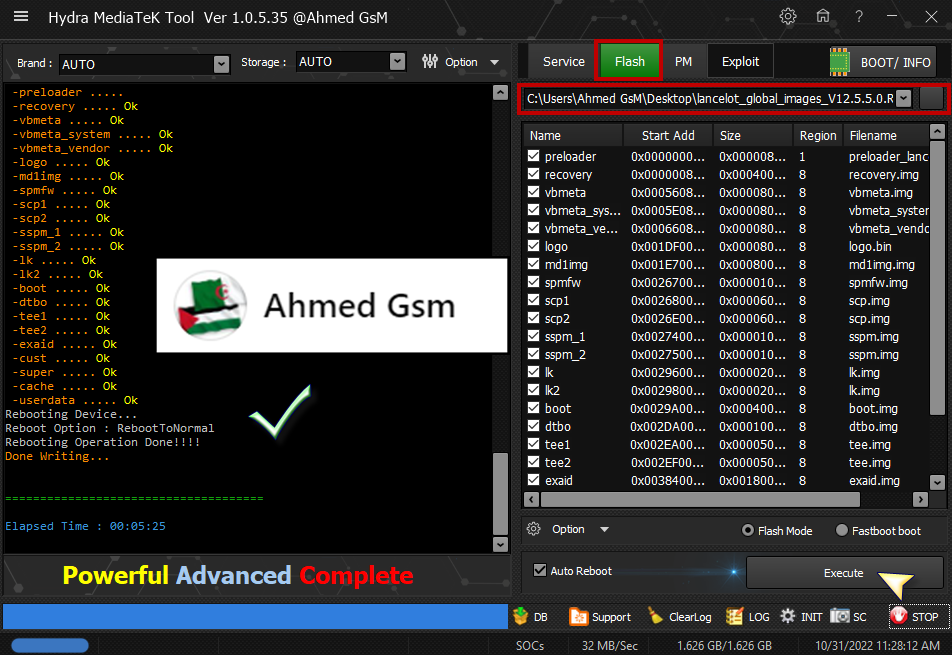
Rebooting Device...
Reboot Option : RebootToNormal
Rebooting Operation Done!!!!
[/FONT][/B]