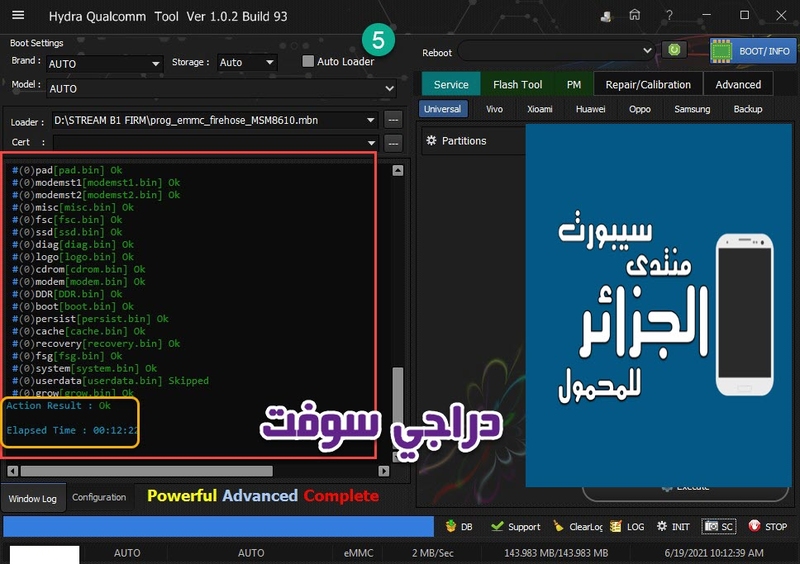
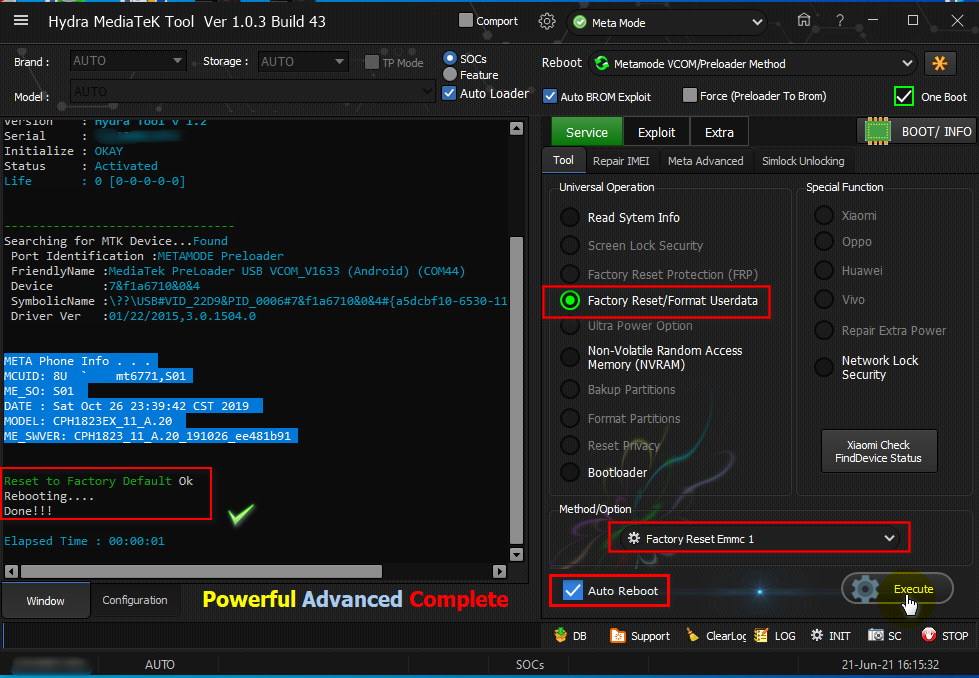
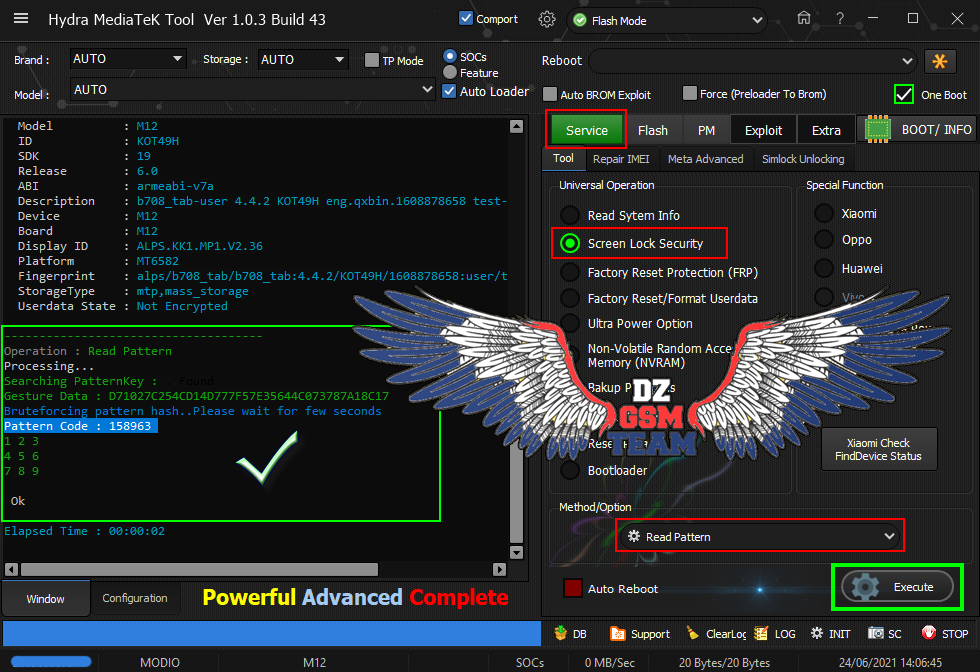
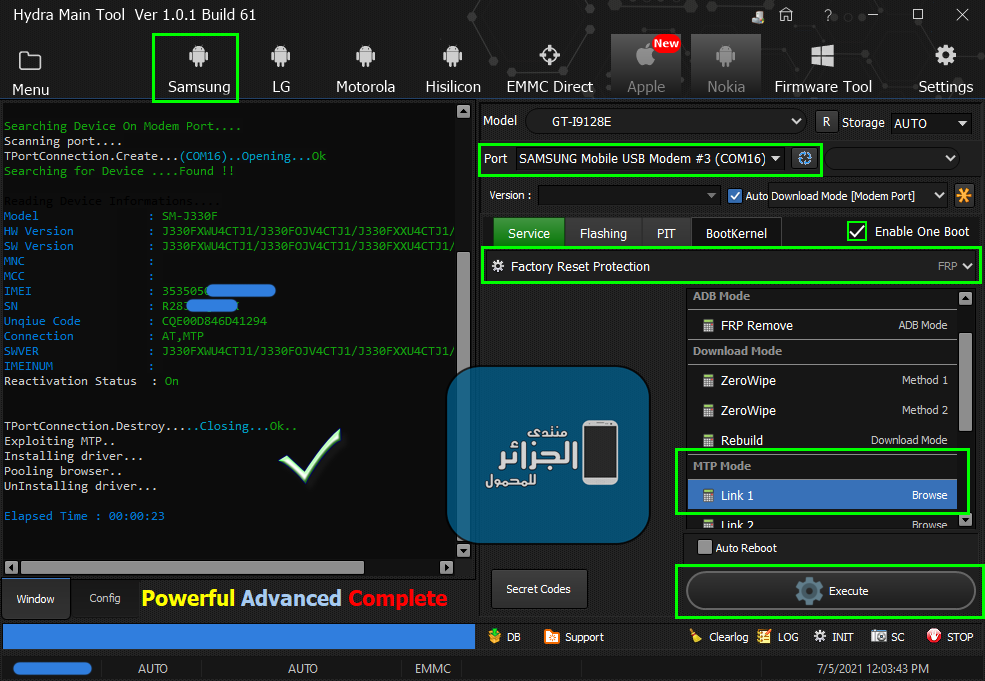
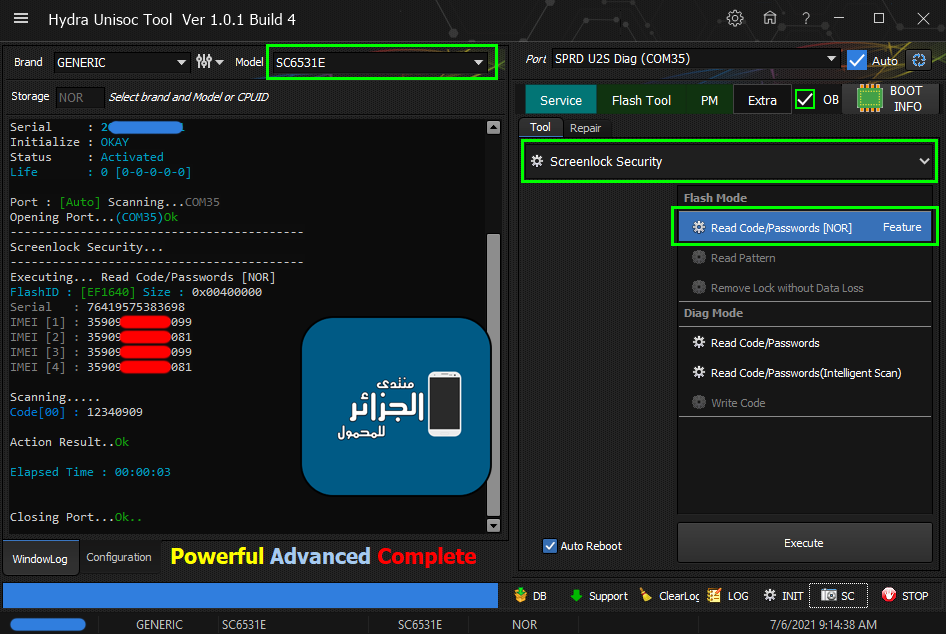
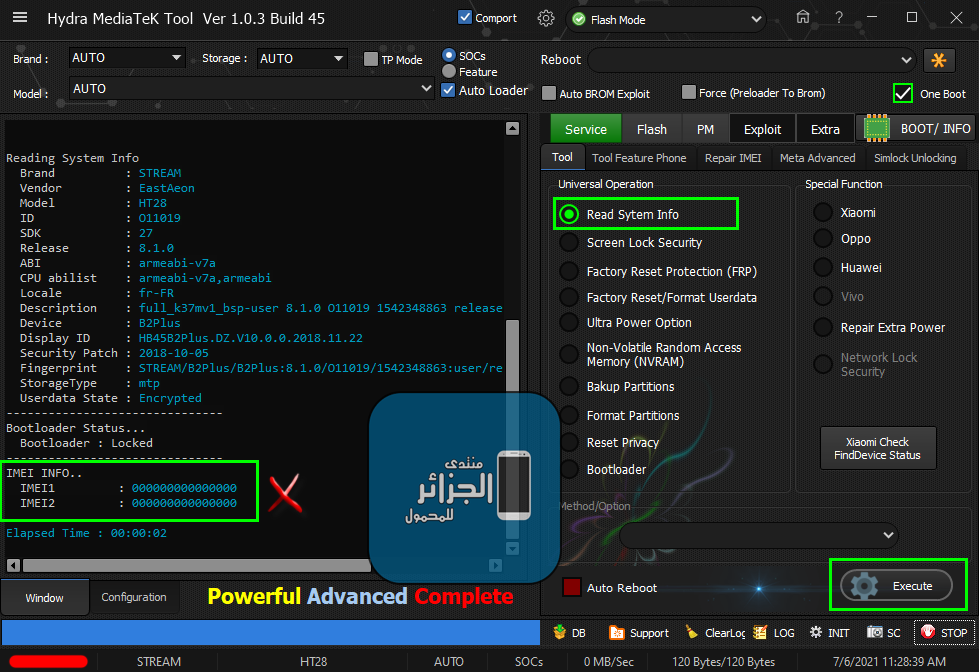
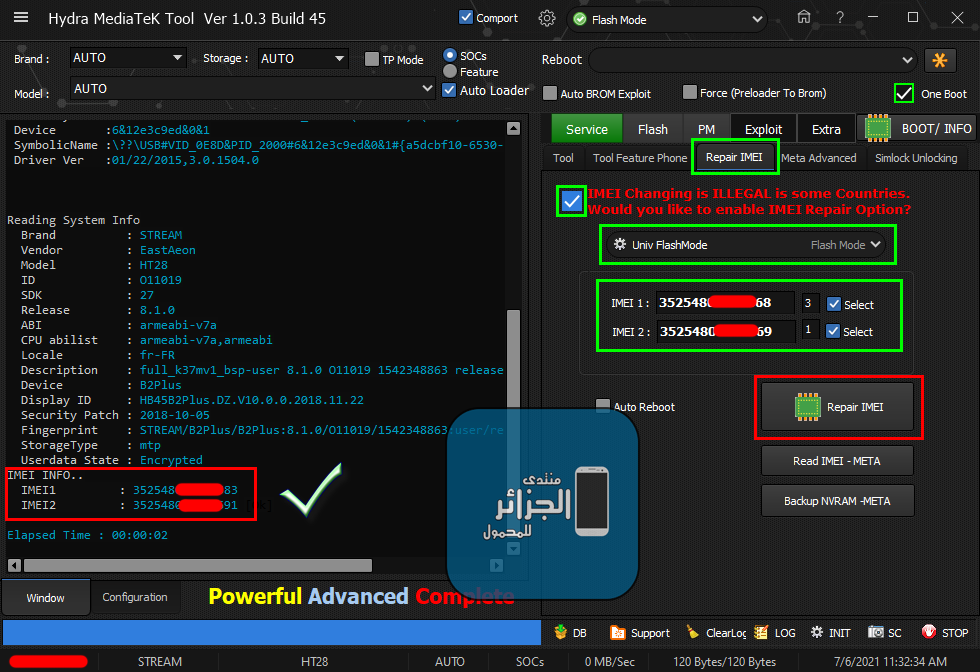
[B][FONT=Arial Black][SIZE=2]Brand : AUTO Model : AUTO Connection : Flash Mode
=====================================
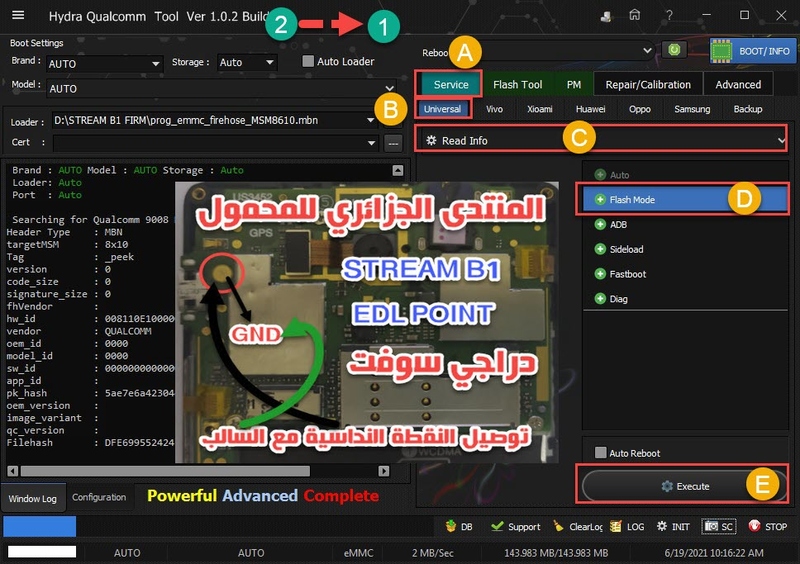
How To Boot : Power off phone
* BROM Mode : Press VOL + or Press VOL -+
* Preloader Mode : Just Insert cable
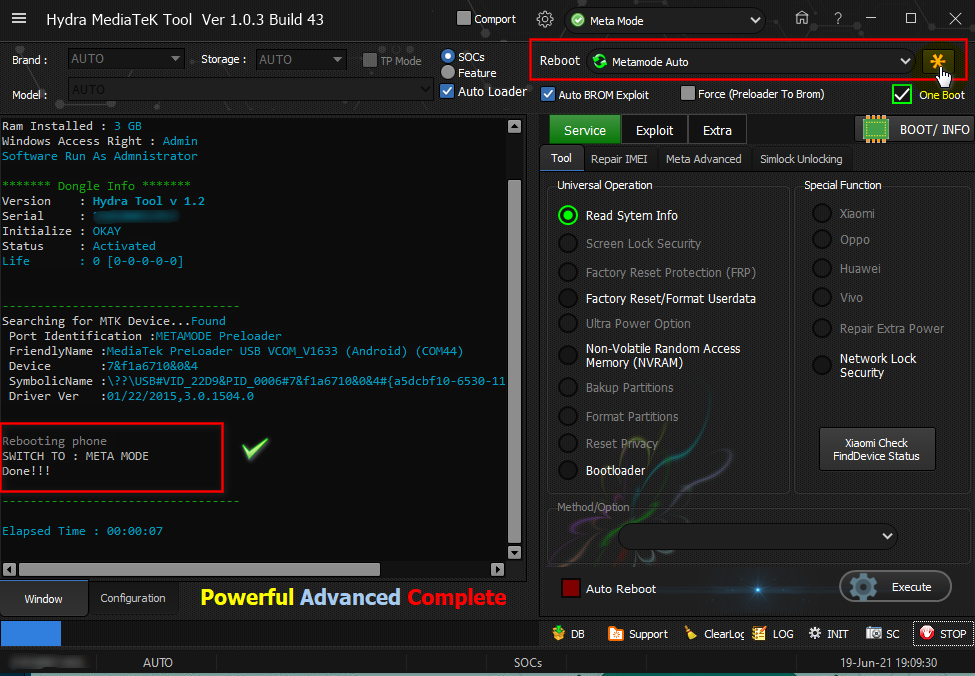
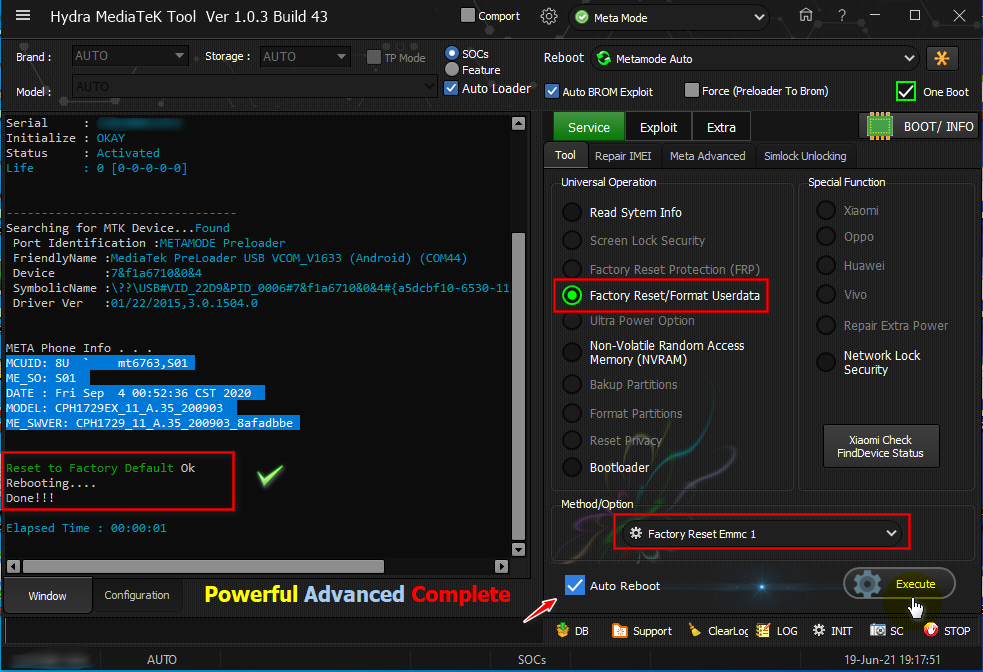
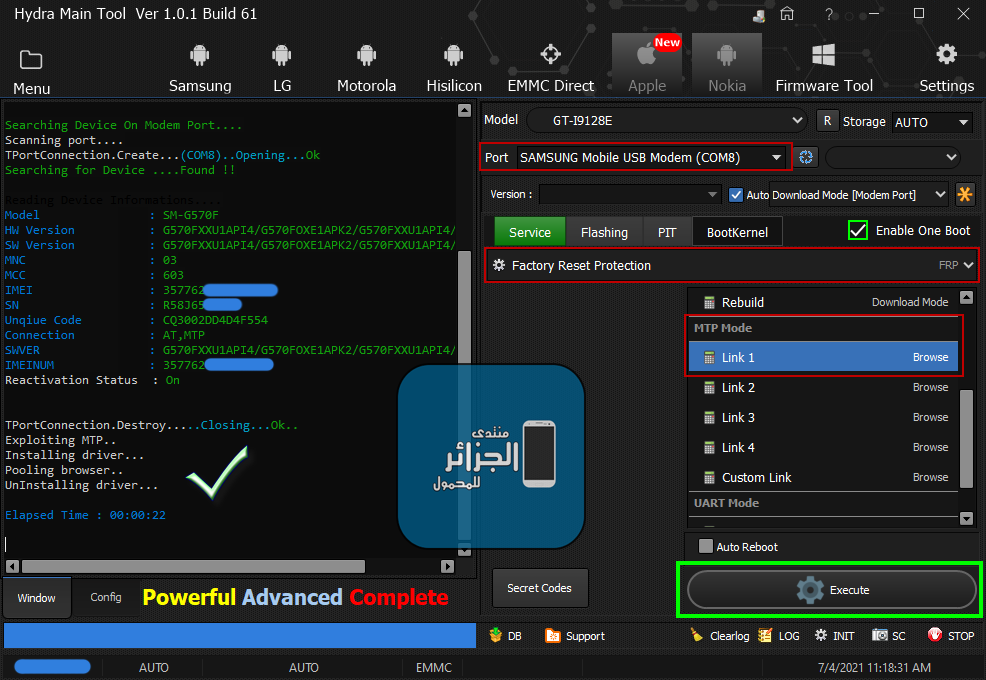
Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM_V1632 (Android) (COM19)
Device :6&12e3c9ed&0&1
SymbolicName :\??\USB#VID_0E8D&PID_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
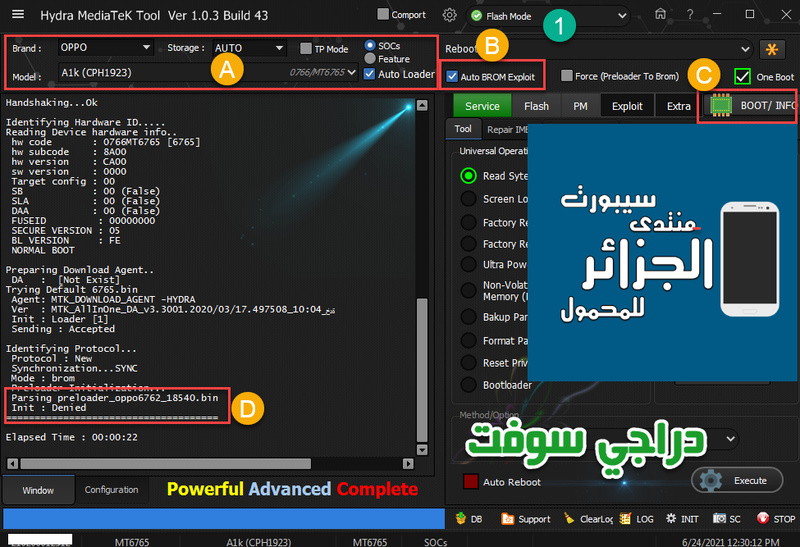
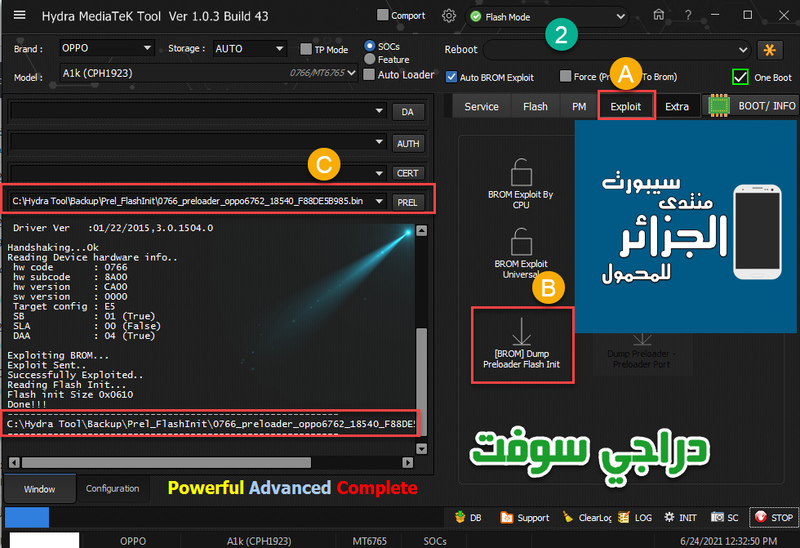
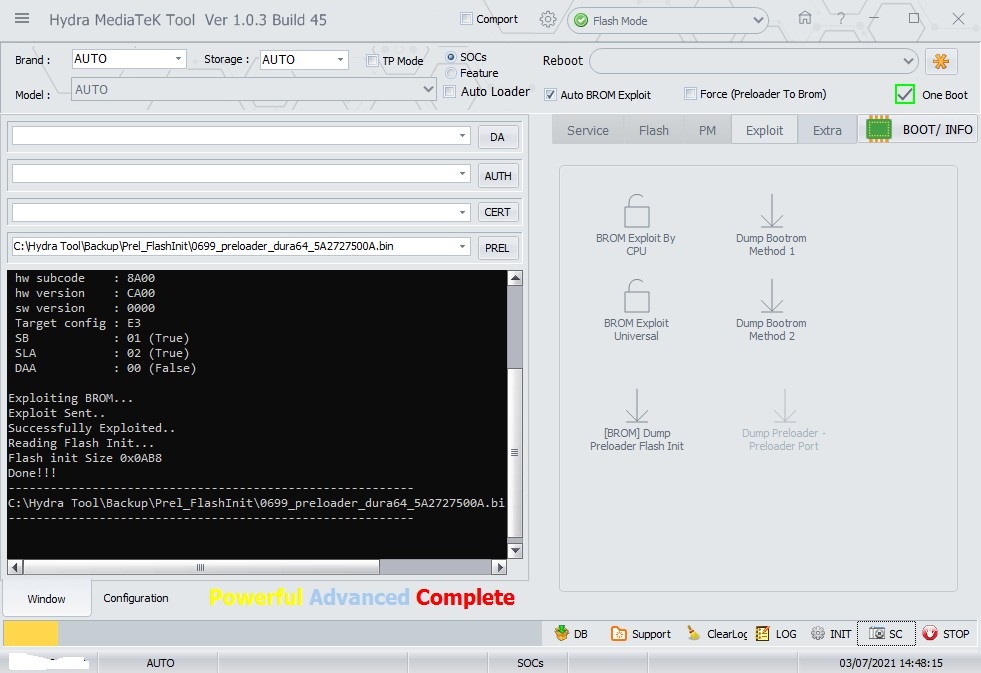
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0699MT6739 [6739]
hw subcode : 8A00
hw version : CB00
sw version : 0002
Target config : 00
SB : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
FUSEID : 00000000
SECURE VERSION : FF
BL VERSION : 03
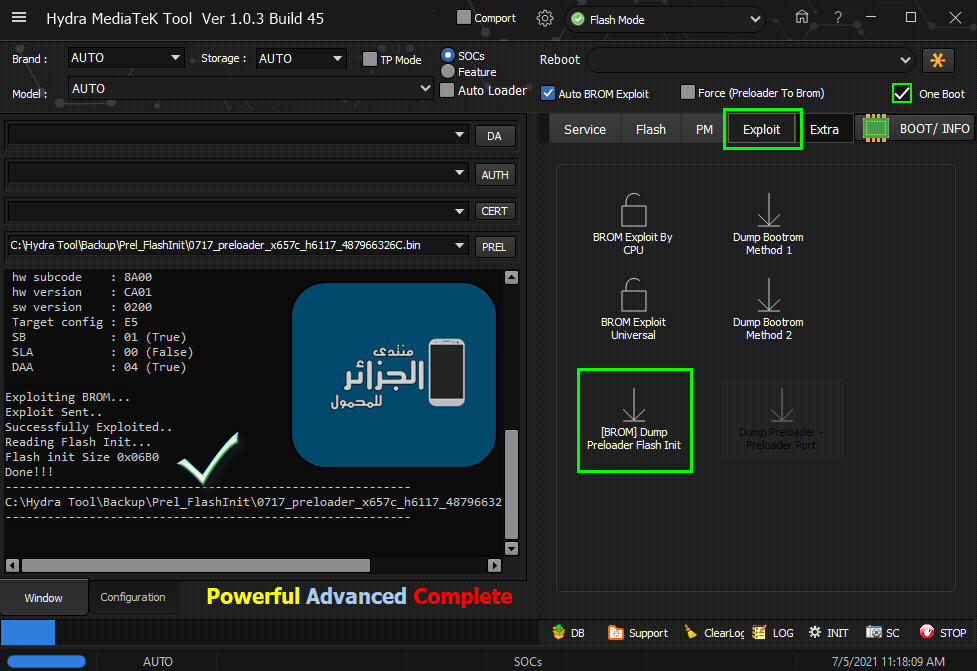
Preparing Download Agent..
DA : 6739.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2020-11-03.22:07_536568
Init : Loader [1]
Sending : Accepted
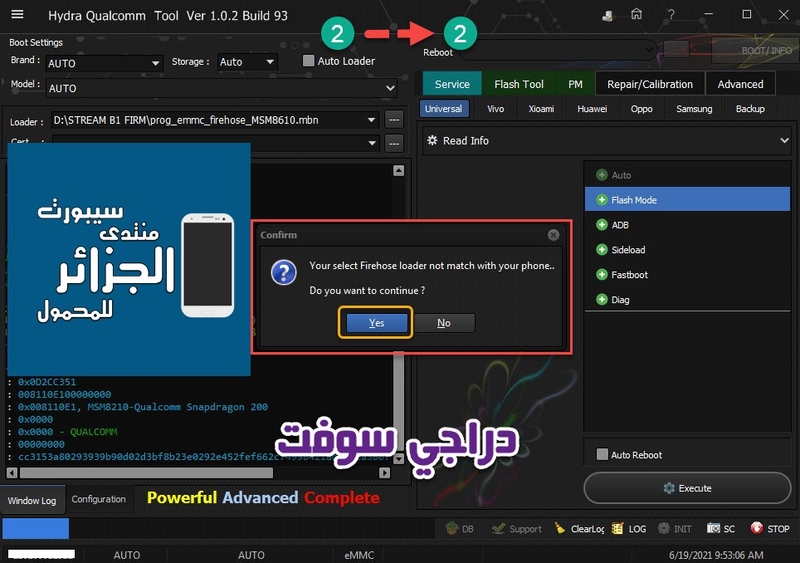
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Mode : preloader
Execute Secondary Loader
Init : Loader [2]
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : FCD05B603F9B7267BFE50420DDC5A2F0
ERAM Size : 0x0000000000020000 -128 KB
IRAM Size : 0x0000000040000000 -1024 MB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x00000001D2000000 -7,281 GB
eMMC CID : 110100303038473330003341A32AC2E3 - 008G30
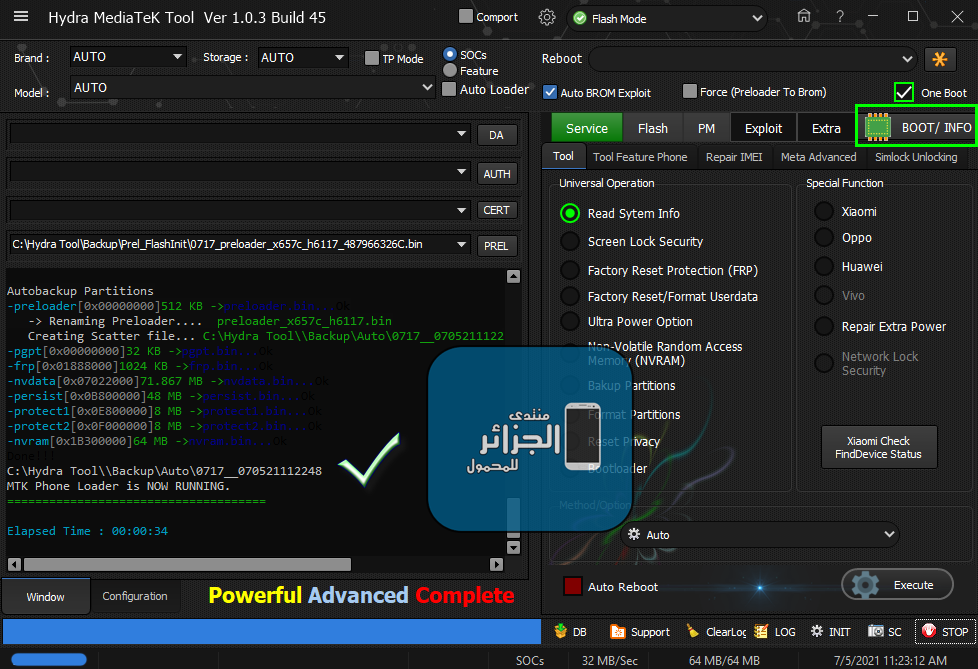
Reading GPT-EMMC [0x00008000] 130 Items
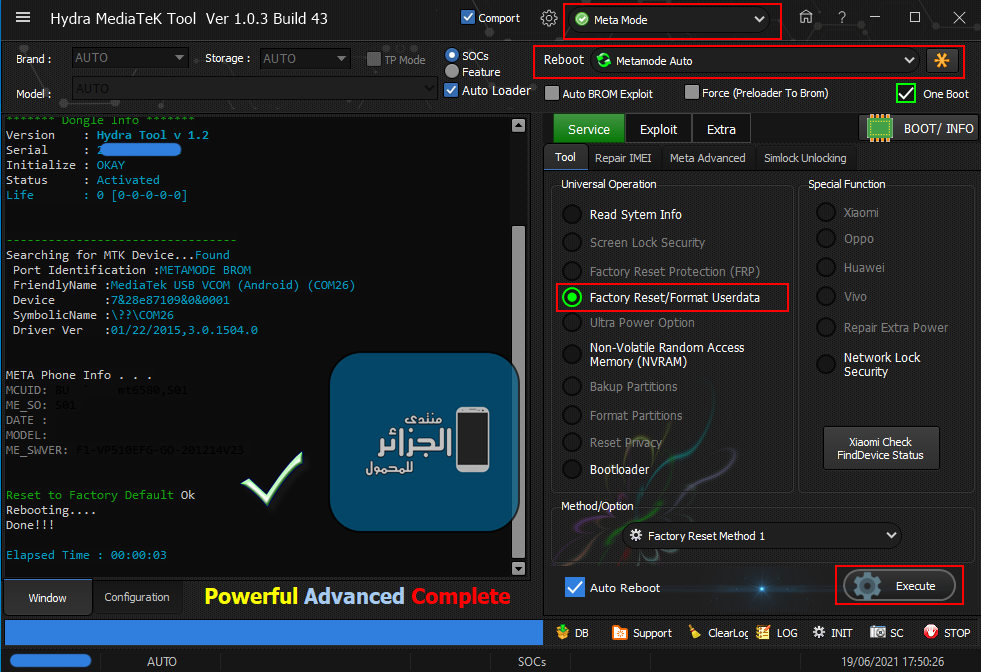
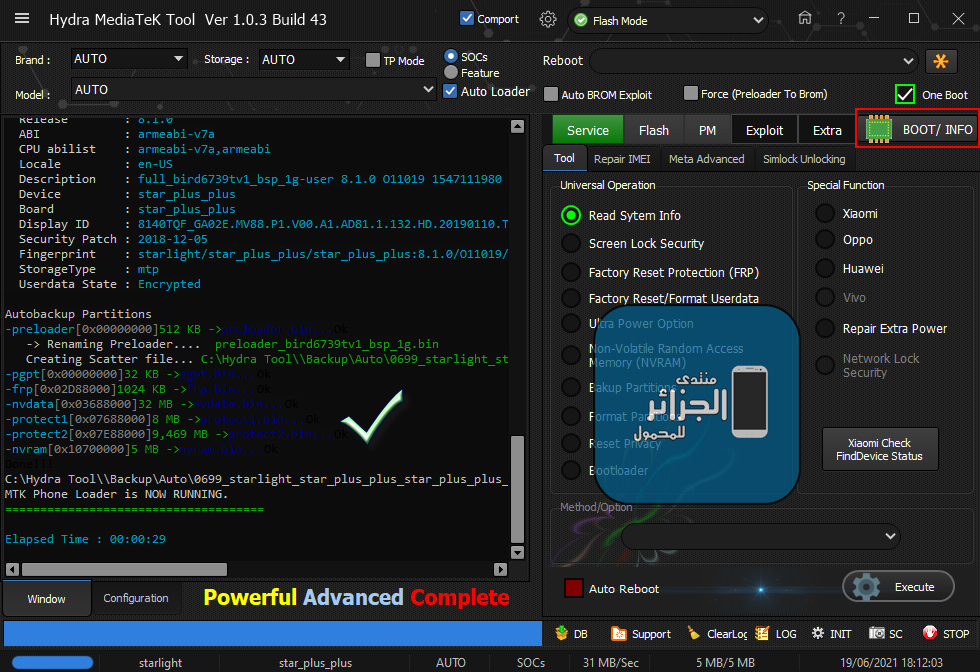
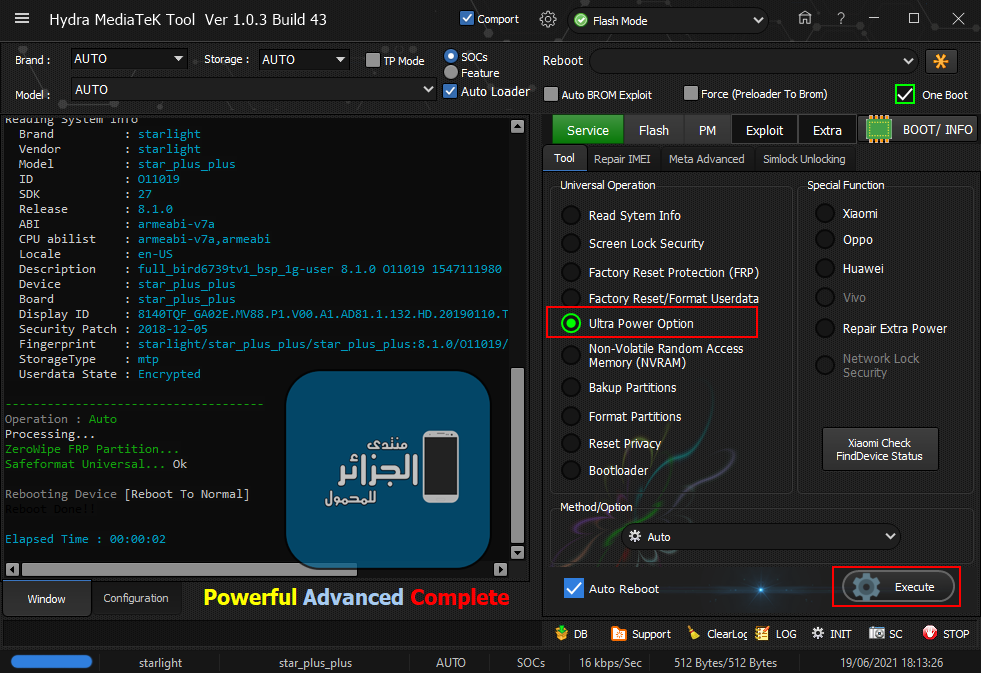
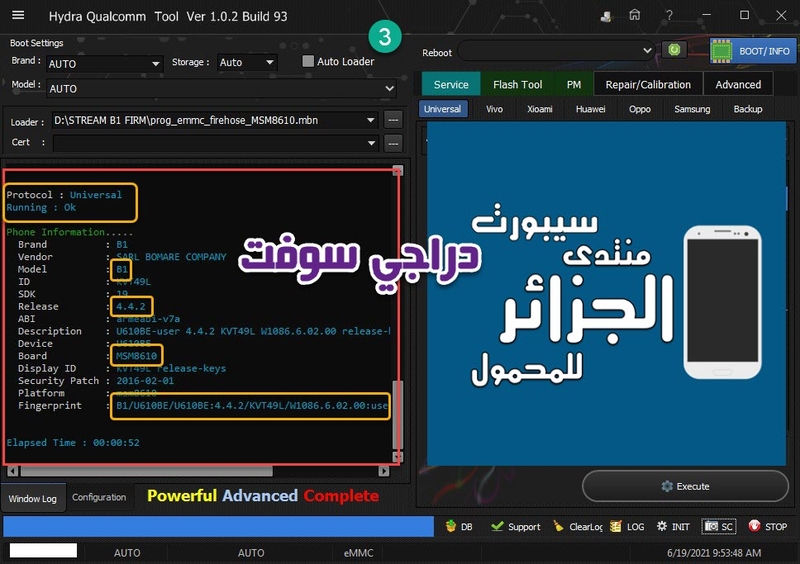
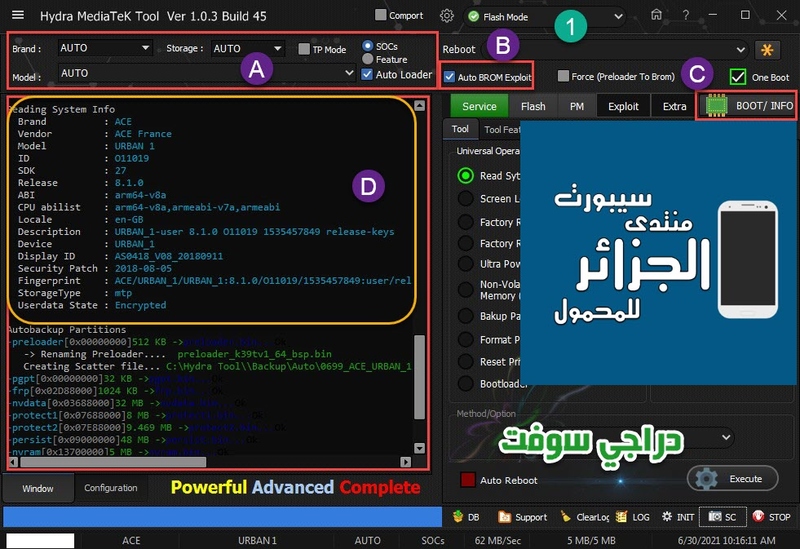
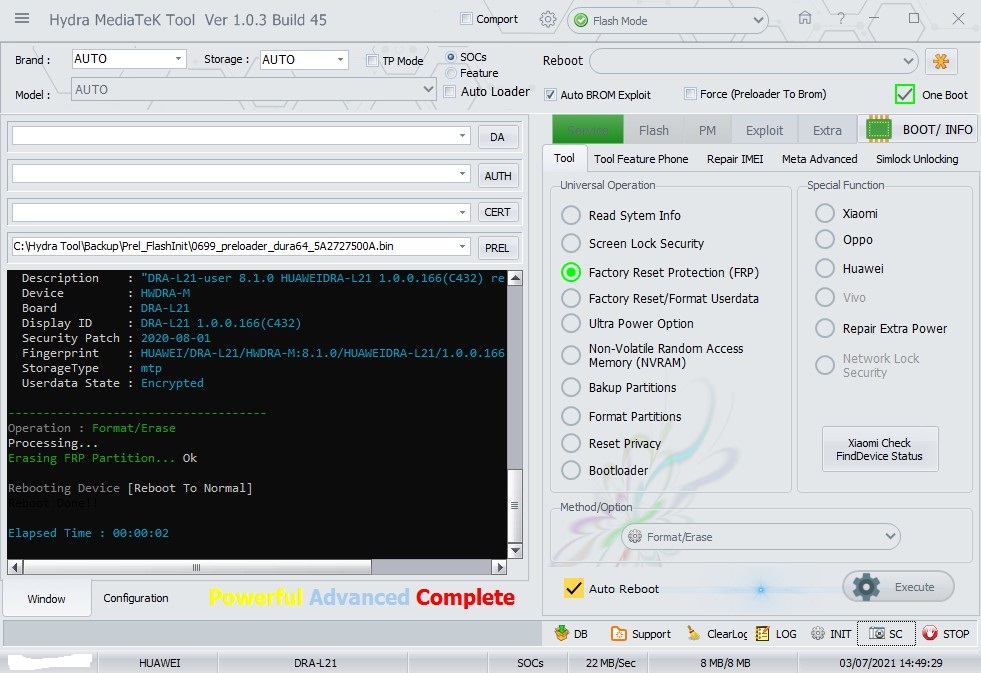
Reading System Info
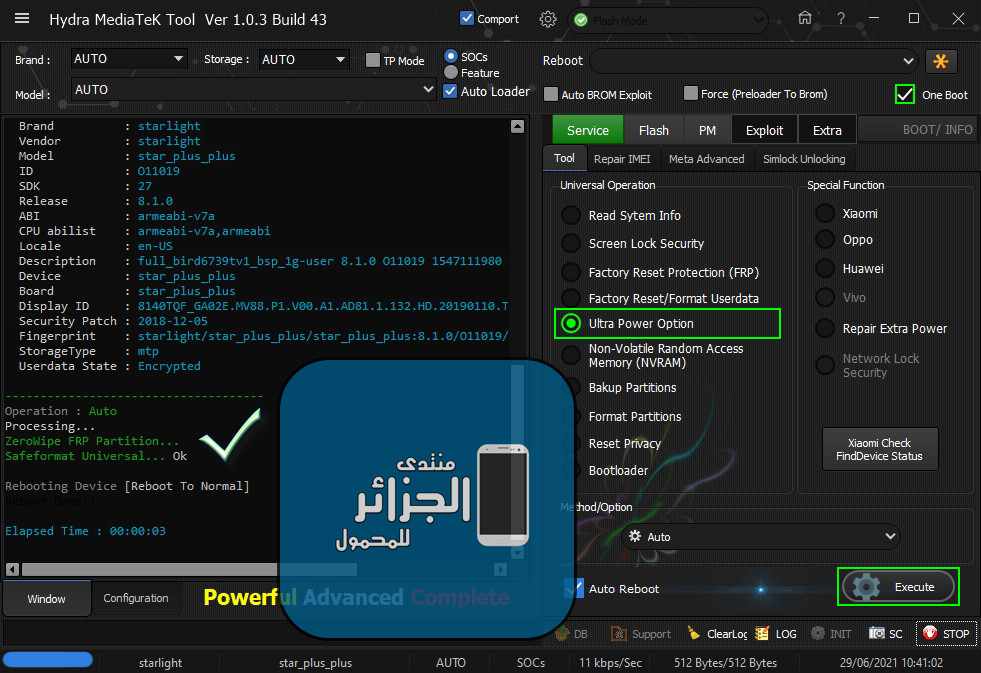
Brand : starlight
Vendor : starlight
Model : star_plus_plus
ID : O11019
SDK : 27
Release : 8.1.0
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-US
Description : full_bird6739tv1_bsp_1g-user 8.1.0 O11019 1547111980 release-keys
Device : star_plus_plus
Board : star_plus_plus
Display ID : 8140TQF_GA02E.MV88.P1.V00.A1.AD81.1.132.HD.20190110.TST.EN
Security Patch : 2018-12-05
Fingerprint : starlight/star_plus_plus/star_plus_plus:8.1.0/O11019/1547111980:user/release-keys
StorageType : mtp
Userdata State : Encrypted
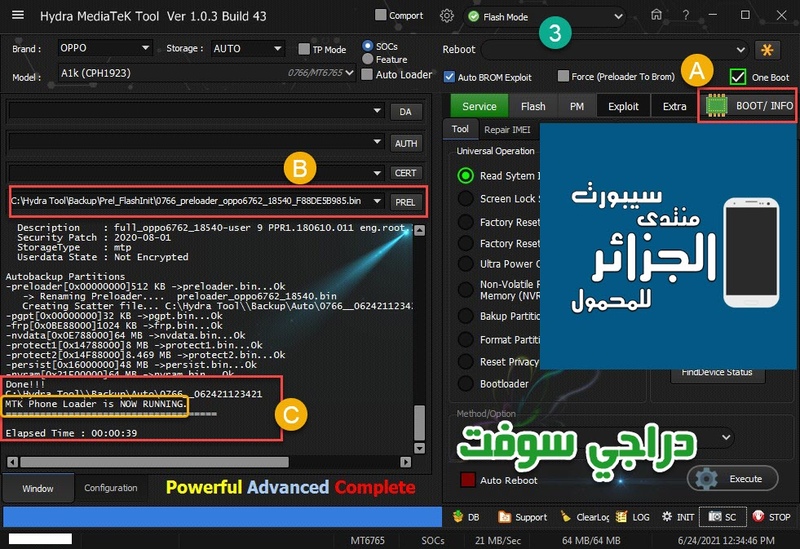
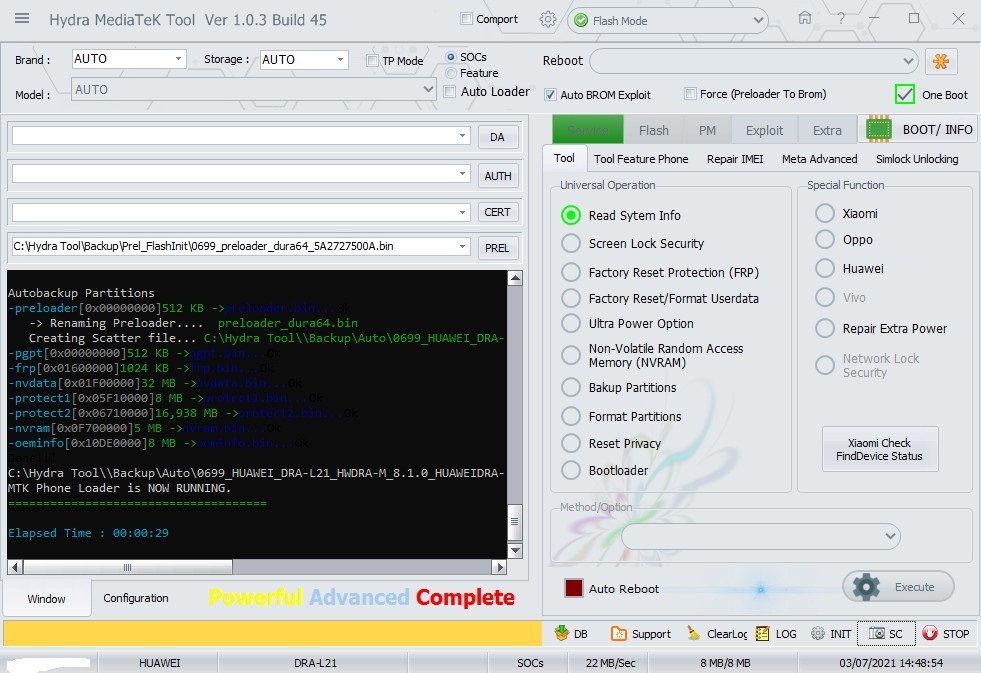
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_bird6739tv1_bsp_1g.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0699_starlight_star_plus_plus_star_plus_plus_8.1.0_O11019_1547111980_061921181129\MT6739_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x02D88000]1024 KB ->frp.bin...Ok
-nvdata[0x03688000]32 MB ->nvdata.bin...Ok
-protect1[0x07688000]8 MB ->protect1.bin...Ok
-protect2[0x07E88000]9,469 MB ->protect2.bin...Ok
-nvram[0x10700000]5 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0699_starlight_star_plus_plus_star_plus_plus_8.1.0_O11019_1547111980_061921181129
MTK Phone Loader is NOW RUNNING.
=====================================
Elapsed Time : 00:00:29
[/SIZE][/FONT][/B]