تثبيت التطبيق
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
ملاحظة: This feature may not be available in some browsers.
أنت تستخدم أحد المتصفحات القديمة. قد لا يتم عرض هذا الموقع أو المواقع الأخرى بشكل صحيح.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
يجب عليك ترقية متصفحك أو استخدام أحد المتصفحات البديلة.
تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
Condor G5 (PHQ520) Flash Done
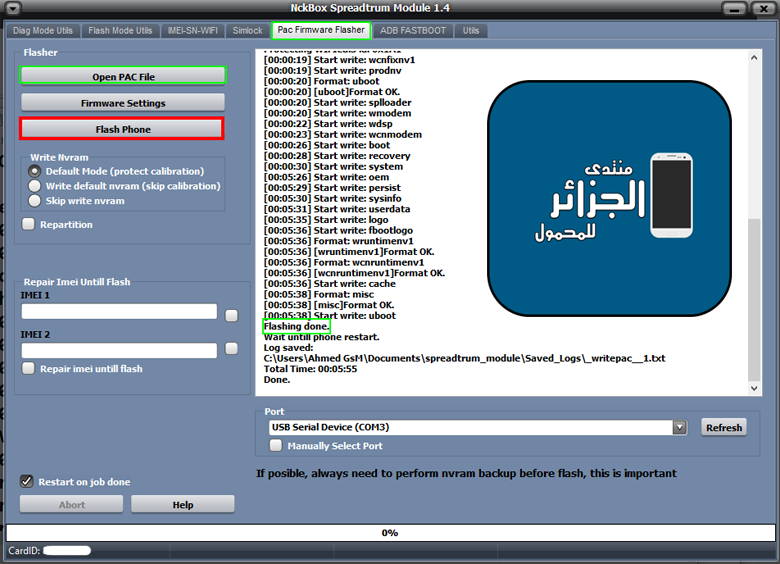
Condor G5 (PHQ520) Flash Done

كود:
[B][FONT=Arial Black][SIZE=2]EXE: NckBox Spreadtrum Module 1.4
ACTION: Flash Firmware.
Selected firmware: zsw609e_Condor_G5_PHQ520.pac
NV: Default Mode (protect calibration)
Device Storage: EMMC
Detected: SCI USB2Serial (COM5)
[00:00:00] Sending loader.
BOOT: ~SPRD3W
~
Sending loader, keep boot key untill loader start.
[00:00:01] Loader ok
[00:00:02] Wait for loader....
Loader OK: ~"Spreadtrum Boot Block version 1.1
Changing bautrate OK.
[00:00:02] First boot done.
[00:00:02] Sending second loader.
[00:00:07] Second loader sent ok.
[00:00:07] Reading: miscdata
[00:00:07] Reading: wfixnv1
NVRAM saved to: C:\Users\Ahmed GsM\Documents\spreadtrum_module\spd_nvram_backup\_3582XXXXXXX707\_3582XXXXXXX707_nvram_backup.tar
[00:00:17] Start write: wfixnv1
Protecting GSM_CALI_ITEM_ID id: 0x2
Protecting W_Calibration id: 0x12D
Protecting BlueTooth id: 0x191
Protecting BandSelect id: 0xD
Protecting WIFI id: 0x199
Protecting MMITest id: 0x19A
Protecting WIFICal1 id: 0x19F
Protecting WIFICal2 id: 0x1A0
Protecting WIFICal3 id: 0x1A1
[00:00:19] Start write: wcnfixnv1
[00:00:19] Start write: prodnv
[00:00:20] Format: uboot
[00:00:20] [uboot]Format OK.
[00:00:20] Start write: splloader
[00:00:20] Start write: wmodem
[00:00:22] Start write: wdsp
[00:00:23] Start write: wcnmodem
[00:00:26] Start write: boot
[00:00:28] Start write: recovery
[00:00:30] Start write: system
[00:05:26] Start write: oem
[00:05:29] Start write: persist
[00:05:30] Start write: sysinfo
[00:05:31] Start write: userdata
[00:05:35] Start write: logo
[00:05:36] Start write: fbootlogo
[00:05:36] Format: wruntimenv1
[00:05:36] [wruntimenv1]Format OK.
[00:05:36] Format: wcnruntimenv1
[00:05:36] [wcnruntimenv1]Format OK.
[00:05:36] Start write: cache
[00:05:38] Format: misc
[00:05:38] [misc]Format OK.
[00:05:38] Start write: uboot
Flashing done.
Wait untill phone restart.
Log saved:
C:\Users\Ahmed GsM\Documents\spreadtrum_module\Saved_Logs\_writepac__1.txt
Total Time: 00:05:55
Done.
[/SIZE][/FONT][/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
Condor G4s (PHQ519) Flash Done
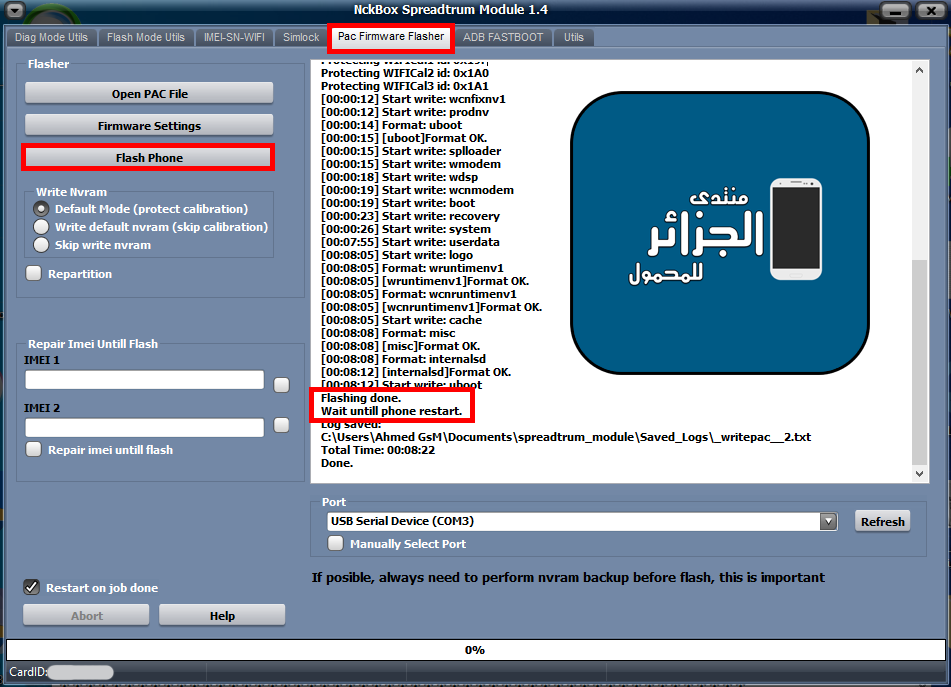
Condor G4s (PHQ519) Flash Done

كود:
[B][FONT=Arial Black][SIZE=2]EXE: NckBox Spreadtrum Module 1.4
ACTION: Flash Firmware.
Selected firmware: sw699_condor.pac
NV: Default Mode (protect calibration)
Device Storage: EMMC
Detected: SCI USB2Serial (COM5)
[00:00:00] Sending loader.
BOOT: ~SPRD3W
~
Sending loader, keep boot key untill loader start.
[00:00:01] Loader ok
[00:00:01] Wait for loader....
Loader OK: ~"Spreadtrum Boot Block version 1.1
Changing bautrate OK.
[00:00:01] First boot done.
[00:00:01] Sending second loader.
[00:00:04] Second loader sent ok.
[00:00:04] Reading: miscdata
[00:00:04] Reading: wfixnv1
NVRAM saved to: C:\Users\Ahmed GsM\Documents\spreadtrum_module\spd_nvram_backup\_3573XXXXXXXX45\_3573XXXXXXXX45_nvram_backup.tar
[00:00:11] Start write: wfixnv1
Protecting GSM_CALI_ITEM_ID id: 0x2
Protecting W_Calibration id: 0x12D
Protecting BlueTooth id: 0x191
Protecting BandSelect id: 0xD
Protecting WIFI id: 0x199
Protecting MMITest id: 0x19A
Protecting WIFICal1 id: 0x19F
Protecting WIFICal2 id: 0x1A0
Protecting WIFICal3 id: 0x1A1
[00:00:12] Start write: wcnfixnv1
[00:00:12] Start write: prodnv
[00:00:14] Format: uboot
[00:00:15] [uboot]Format OK.
[00:00:15] Start write: splloader
[00:00:15] Start write: wmodem
[00:00:18] Start write: wdsp
[00:00:19] Start write: wcnmodem
[00:00:19] Start write: boot
[00:00:23] Start write: recovery
[00:00:26] Start write: system
[00:07:55] Start write: userdata
[00:08:05] Start write: logo
[00:08:05] Format: wruntimenv1
[00:08:05] [wruntimenv1]Format OK.
[00:08:05] Format: wcnruntimenv1
[00:08:05] [wcnruntimenv1]Format OK.
[00:08:05] Start write: cache
[00:08:08] Format: misc
[00:08:08] [misc]Format OK.
[00:08:08] Format: internalsd
[00:08:12] [internalsd]Format OK.
[00:08:12] Start write: uboot
[COLOR="#FF0000"]Flashing done.
Wait untill phone restart.
Log saved:
C:\Users\Ahmed GsM\Documents\spreadtrum_module\Saved_Logs\_writepac__2.txt
Total Time: 00:08:22
Done.
[/COLOR][/SIZE][/FONT][/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
Lenovo A1000 Safe Format Userdata
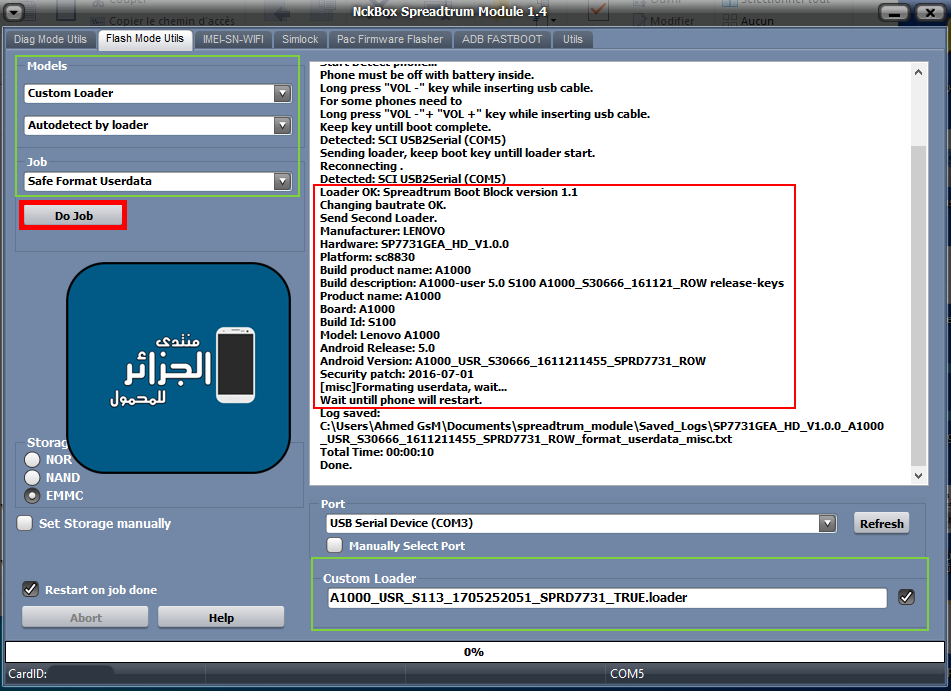
Lenovo A1000 Safe Format Userdata

كود:
[B][FONT=Arial Black][SIZE=2]Custom loader: A1000_USR_S113_1705252051_SPRD7731_TRUE.loader
Phone Storage: EMMC
EXE: NckBox Spreadtrum Module 1.4
SELECTED: Autodetect by loader
ACTION: Format Userdata(misc)
Custom loader: A1000_USR_S113_1705252051_SPRD7731_TRUE.loader
Start Detect phone...
Phone must be off with battery inside.
Long press "VOL -" key while inserting usb cable.
For some phones need to
Long press "VOL -"+ "VOL +" key while inserting usb cable.
Keep key untill boot complete.
Detected: SCI USB2Serial (COM5)
Sending loader, keep boot key untill loader start.
Reconnecting .
Detected: SCI USB2Serial (COM5)
Loader OK: Spreadtrum Boot Block version 1.1
Changing bautrate OK.
Send Second Loader.
Manufacturer: LENOVO
Hardware: SP7731GEA_HD_V1.0.0
Platform: sc8830
Build product name: A1000
Build description: A1000-user 5.0 S100 A1000_S30666_161121_ROW release-keys
Product name: A1000
Board: A1000
Build Id: S100
Model: Lenovo A1000
Android Release: 5.0
Android Version: A1000_USR_S30666_1611211455_SPRD7731_ROW
Security patch: 2016-07-01
[misc]Formating userdata, wait...
Wait untill phone will restart.
Log saved:
C:\Users\Ahmed GsM\Documents\spreadtrum_module\Saved_Logs\SP7731GEA_HD_V1.0.0_A1000_USR_S30666_1611211455_SPRD7731_ROW_format_userdata_misc.txt
Total Time: 00:00:10
Done.
[/SIZE][/FONT][/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
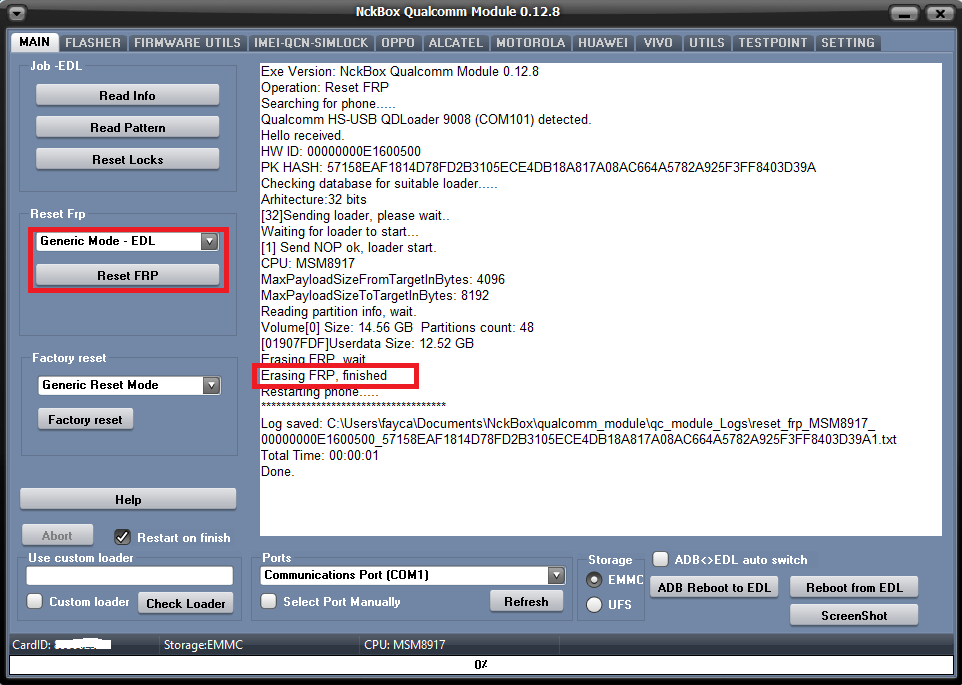
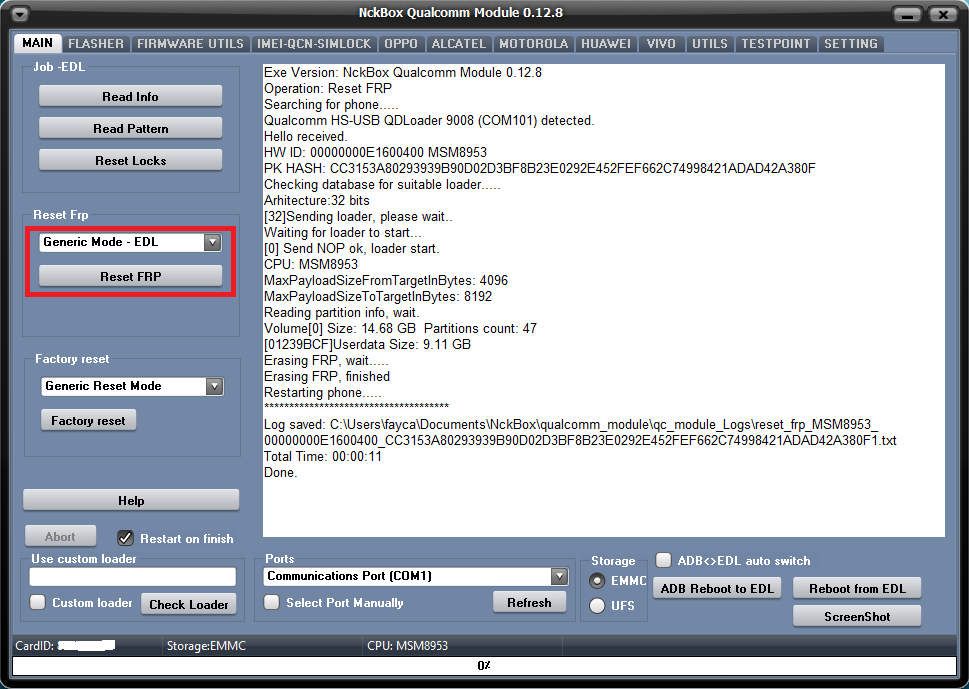
ALCATEL 5051D
كود:
Exe Version: NckBox Qualcomm Module 0.12.8
Operation: Read Info
Searching for phone.....
Qualcomm HS-USB QDLoader 9008 (COM31) detected.
Hello received.
HW ID: 00000000E1009600 MSM8909
PK HASH: CC3153A80293939B90D02D3BF8B23E0292E452FEF662C74998421ADAD42A380F
Checking database for suitable loader.....
Arhitecture:32 bits
[32]Sending loader, please wait..
Waiting for loader to start...
[1] Send NOP ok, loader start.
CPU: MSM8909
MaxPayloadSizeFromTargetInBytes: 4096
MaxPayloadSizeToTargetInBytes: 8192
Reading partition info, wait.
Volume[0] Size: 7,28 GB Partitions count: 36
[0084F3DF]Userdata Size: 4,15 GB
Manufacturer: TCL
Cpu: armeabi-v7a
Build Id: MMB29M
Model: 5051D
Android Release: 6.0.1
Android Version: MMB29M release-keys
Config: default,diag,serial_smd,serial_tty,adb
Security patch: 2016-05-01
IMEI: 357368072686447
Model: 5051D-2AALDZ1-1
Secro: XPA0HM00BR20
Restarting phone.....FRP remove
كود:
Exe Version: NckBox Qualcomm Module 0.12.8
Operation: Reset FRP
Searching for phone.....
Qualcomm HS-USB QDLoader 9008 (COM31) detected.
Hello received.
HW ID: 00000000E1009600 MSM8909
PK HASH: CC3153A80293939B90D02D3BF8B23E0292E452FEF662C74998421ADAD42A380F
Checking database for suitable loader.....
Arhitecture:32 bits
[32]Sending loader, please wait..
Waiting for loader to start...
[1] Send NOP ok, loader start.
CPU: MSM8909
MaxPayloadSizeFromTargetInBytes: 4096
MaxPayloadSizeToTargetInBytes: 8192
Reading partition info, wait.
Volume[0] Size: 7,28 GB Partitions count: 36
[0084F3DF]Userdata Size: 4,15 GB
Erasing Alcatel FRP, wait.....
Erasing FRP, finished
Restarting phone.....READ FIRMWARE
كود:
Exe Version: NckBox Qualcomm Module 0.12.8
Operation: Dump Firmware
Searching for phone.....
Qualcomm HS-USB QDLoader 9008 (COM31) detected.
Hello received.
HW ID: 00000000E1009600 MSM8909
PK HASH: CC3153A80293939B90D02D3BF8B23E0292E452FEF662C74998421ADAD42A380F
Checking database for suitable loader.....
Arhitecture:32 bits
[32]Sending loader, please wait..
Waiting for loader to start...
[1] Send NOP ok, loader start.
CPU: MSM8909
MaxPayloadSizeFromTargetInBytes: 4096
MaxPayloadSizeToTargetInBytes: 8192
Reading partition info, wait.
Volume[0] Size: 7,28 GB Partitions count: 36
[0084F3DF]Userdata Size: 4,15 GB
IMEI: 357368072686447
Model: 5051D-2AALDZ1-1
Secro: XPA0HM00BR20
Manufacturer: TCL
Cpu: armeabi-v7a
Build Id: MMB29M
Model: 5051D
Android Release: 6.0.1
Android Version: MMB29M release-keys
Config: default,diag,serial_smd,serial_tty,adb
Security patch: 2016-05-01
[0] [ PrimaryGPT ] Reading: gpt_main0.bin
[0] [ BackupGPT ] Reading: gpt_backup0.bin
[0] [ modem ] Reading: NON-HLOS.bin
[0] [ sbl1 ] Reading: sbl1.mbn
[0] [ aboot ] Reading: emmc_appsboot.mbn
[0] [ rpm ] Reading: rpm.mbn
[0] [ tz ] Reading: tz.mbn
[0] [ boot ]Reading: boot.img
[0] [ fsg ] Reading: study.tar
[0] [ sec ] Reading: sec.dat
[0] [ traceability ] Reading: traceability.mbn
[0] [ mobile_info ]Reading: mobile_info.img
[0] [ splash ] Reading: splash.img
[0] [ misc ] Reading: misc.img
[0] [ cache ]Reading: cache.img
[0] [ system ] Reading: system.img
[0] [ recovery ]Reading: recovery.img
[0] [ userdata ]Reading: userdata.img
Saved to: C:\Users\LLCOOLR\Documents\NckBox\qualcomm_module\qc_firmware\TCL_MMB29M_5051D_6_0_1_357368072686447_5051D-2AALDZ1-1_XPA0HM00BR20\
Restarting phone.....رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
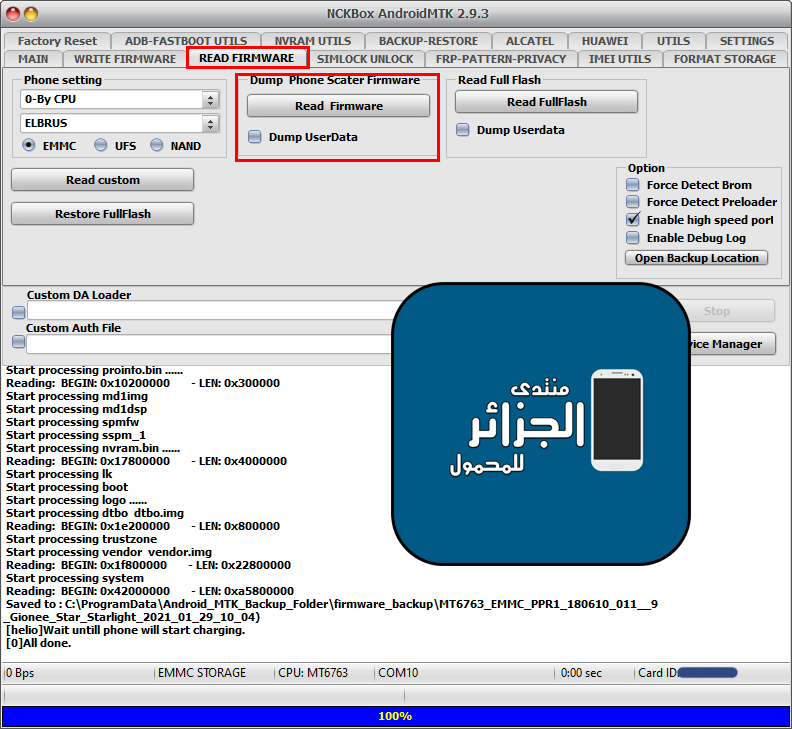
Starlight Gionee Star
Boot Info + Reset To Factory + Reset FRP + Read Firmware
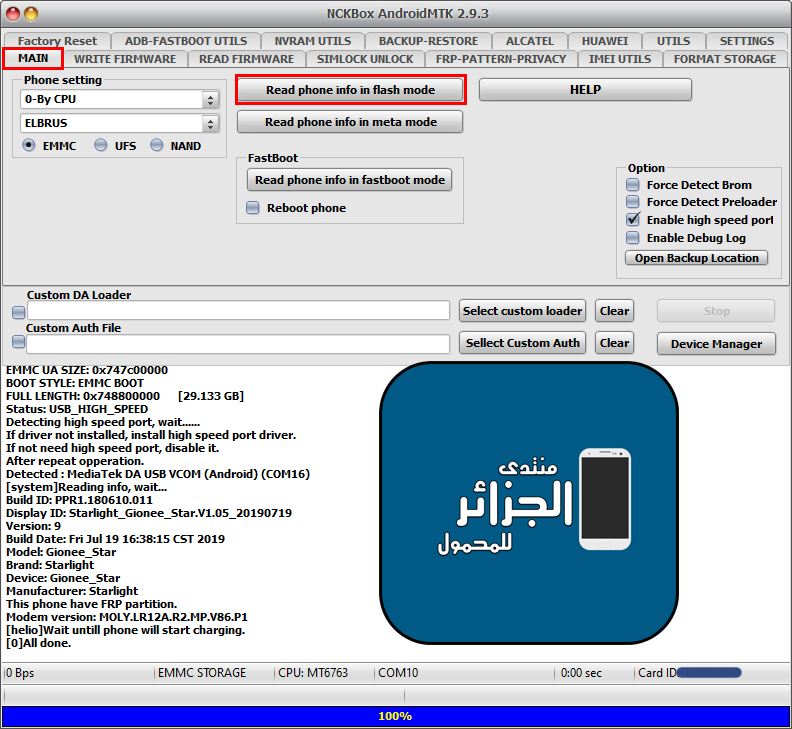
Boot Info
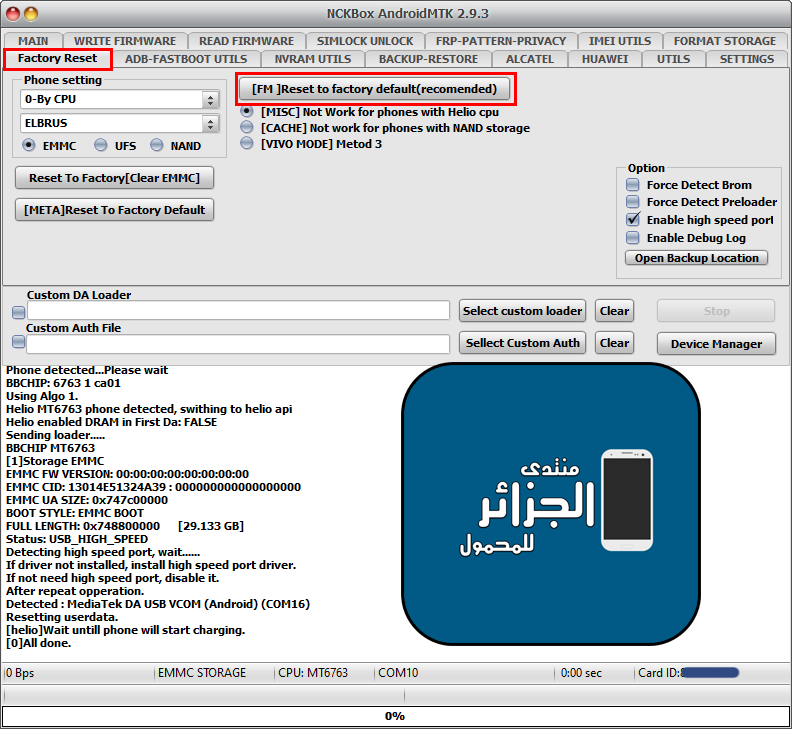
Reset To Factory
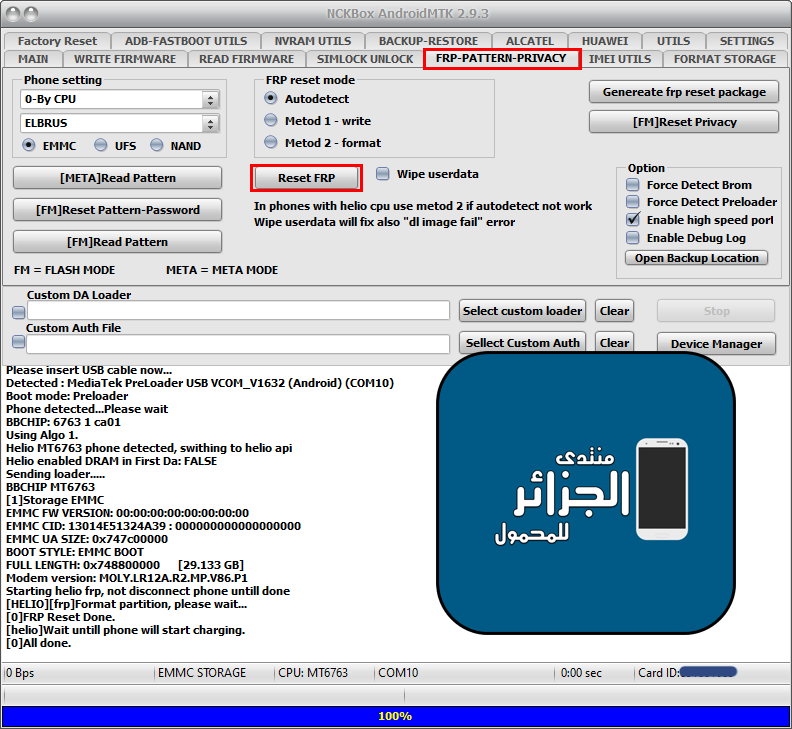
Reset FRP
Read Firmware
Starlight Gionee Star
Boot Info + Reset To Factory + Reset FRP + Read Firmware
Boot Info

كود:
[B][FONT=Arial Black][SIZE=2] Action : Boot Info.
Selected 0-By CPU:ELBRUS
Exe version: NCKBox AndroidMTK 2.9.3
Reinsert phone battery.
Battery must be charged.
Phone must be off with battery inside.
Please insert USB cable now...
Detected : MediaTek PreLoader USB VCOM_V1632 (Android) (COM10)
Boot mode: Preloader
Phone detected...Please wait
BBCHIP: 6763 1 ca01
Using Algo 1.
Helio MT6763 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6763
[1]Storage EMMC
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 13014E51324A39 : 000000000000000000
EMMC UA SIZE: 0x747c00000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x748800000 [29.133 GB]
Status: USB_HIGH_SPEED
Detecting high speed port, wait......
If driver not installed, install high speed port driver.
If not need high speed port, disable it.
After repeat opperation.
Detected : MediaTek DA USB VCOM (Android) (COM16)
[COLOR="#FF0000"] [system]Reading info, wait...
Build ID: PPR1.180610.011
Display ID: Starlight_Gionee_Star.V1.05_20190719
Version: 9
Build Date: Fri Jul 19 16:38:15 CST 2019
Model: Gionee_Star
Brand: Starlight
Device: Gionee_Star
Manufacturer: Starlight
This phone have FRP partition.
Modem version: MOLY.LR12A.R2.MP.V86.P1
[helio]Wait untill phone will start charging.
[0]All done.
[/COLOR][/SIZE][/FONT][/B]Reset To Factory

كود:
[B][FONT=Arial Black][SIZE=2] [MISC]Action: Reset To Factory.
Selected 0-By CPU:ELBRUS
Exe version: NCKBox AndroidMTK 2.9.3
Reinsert phone battery.
Battery must be charged.
Phone must be off with battery inside.
Please insert USB cable now...
Detected : MediaTek PreLoader USB VCOM_V1632 (Android) (COM10)
Boot mode: Preloader
Phone detected...Please wait
BBCHIP: 6763 1 ca01
Using Algo 1.
Helio MT6763 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6763
[1]Storage EMMC
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 13014E51324A39 : 000000000000000000
EMMC UA SIZE: 0x747c00000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x748800000 [29.133 GB]
Status: USB_HIGH_SPEED
Detecting high speed port, wait......
If driver not installed, install high speed port driver.
If not need high speed port, disable it.
After repeat opperation.
Detected : MediaTek DA USB VCOM (Android) (COM16)
[COLOR="#FF0000"] Resetting userdata.
[helio]Wait untill phone will start charging.
[0]All done.
[/COLOR][/SIZE][/FONT][/B]Reset FRP

كود:
[B][FONT=Arial Black][SIZE=2] Exe version: NCKBox AndroidMTK 2.9.3
Selected model: 0-By CPU ELBRUS
[auto]Action: Reset FRP
Reinsert phone battery.
Battery must be charged.
Phone must be off with battery inside.
Please insert USB cable now...
Detected : MediaTek PreLoader USB VCOM_V1632 (Android) (COM10)
Boot mode: Preloader
Phone detected...Please wait
BBCHIP: 6763 1 ca01
Using Algo 1.
Helio MT6763 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6763
[1]Storage EMMC
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 13014E51324A39 : 000000000000000000
EMMC UA SIZE: 0x747c00000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x748800000 [29.133 GB]
Modem version: MOLY.LR12A.R2.MP.V86.P1
Starting helio frp, not disconnect phone untill done
[COLOR="#FF0000"] [HELIO][frp]Format partition, please wait...
[0]FRP Reset Done.
[helio]Wait untill phone will start charging.
[0]All done.
[/COLOR][/SIZE][/FONT][/B]Read Firmware

كود:
[B][FONT=Arial Black][SIZE=2] Action : Read Firmware.
Selected 0-By CPU:ELBRUS
Exe version: NCKBox AndroidMTK 2.9.3
Reinsert phone battery.
Battery must be charged.
Phone must be off with battery inside.
Please insert USB cable now...
Detected : MediaTek PreLoader USB VCOM_V1632 (Android) (COM10)
Boot mode: Preloader
Phone detected...Please wait
BBCHIP: 6763 1 ca01
Using Algo 1.
Helio MT6763 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6763
[1]Storage EMMC
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 13014E51324A39 : 000000000000000000
EMMC UA SIZE: 0x747c00000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x748800000 [29.133 GB]
Status: USB_HIGH_SPEED
Detecting high speed port, wait......
If driver not installed, install high speed port driver.
If not need high speed port, disable it.
After repeat opperation.
Detected : MediaTek DA USB VCOM (Android) (COM16)
[COLOR="#FF0000"] [system]Reading info, wait...
Build ID: PPR1.180610.011
Display ID: Starlight_Gionee_Star.V1.05_20190719
Version: 9
Build Date: Fri Jul 19 16:38:15 CST 2019
Model: Gionee_Star
Brand: Starlight
Device: Gionee_Star
Manufacturer: Starlight
Modem version: MOLY.LR12A.R2.MP.V86.P1
[/COLOR] [COLOR="#008000"]Start dumping flash, this can take up to 1 hour.......
Dumping Preloader.
Partition: boot_para
Partition: recovery
Partition: para
Partition: expdb
Partition: frp
Partition: nvcfg
Partition: nvdata
Partition: metadata
Partition: protect1
Partition: protect2
Partition: seccfg
Partition: persist
Partition: sec1
Partition: proinfo
Partition: md1img
Partition: md1dsp
Partition: spmfw
Partition: sspm_1
Partition: sspm_2
Partition: gz1
Partition: gz2
Partition: nvram
Partition: lk
Partition: lk2
Partition: boot
Partition: logo
Partition: dtbo
Partition: tee1
Partition: tee2
Partition: teksunhw
Partition: vendor
Partition: system
Partition: cache
Partition: userdata
Partition: flashinfo
Start processing recovery
Start processing protect1.img ......
Reading: BEGIN: 0xb688000 - LEN: 0x800000
Start processing protect2.img ......
Reading: BEGIN: 0xbe88000 - LEN: 0x978000
Start processing proinfo.bin ......
Reading: BEGIN: 0x10200000 - LEN: 0x300000
Start processing md1img
Start processing md1dsp
Start processing spmfw
Start processing sspm_1
Start processing nvram.bin ......
Reading: BEGIN: 0x17800000 - LEN: 0x4000000
Start processing lk
Start processing boot
Start processing logo ......
Start processing dtbo dtbo.img
Reading: BEGIN: 0x1e200000 - LEN: 0x800000
Start processing trustzone
Start processing vendor vendor.img
Reading: BEGIN: 0x1f800000 - LEN: 0x22800000
Start processing system
Reading: BEGIN: 0x42000000 - LEN: 0xa5800000
Saved to : C:\ProgramData\Android_MTK_Backup_Folder\firmware_backup\MT6763_EMMC_PPR1_180610_011__9_Gionee_Star_Starlight_2021_01_29_10_04)
[helio]Wait untill phone will start charging.
[0]All done[/COLOR].
[/SIZE][/FONT][/B]- إنضم
- 16 سبتمبر 2012
- المشاركات
- 3,595
- مستوى التفاعل
- 3,276
- النقاط
- 113
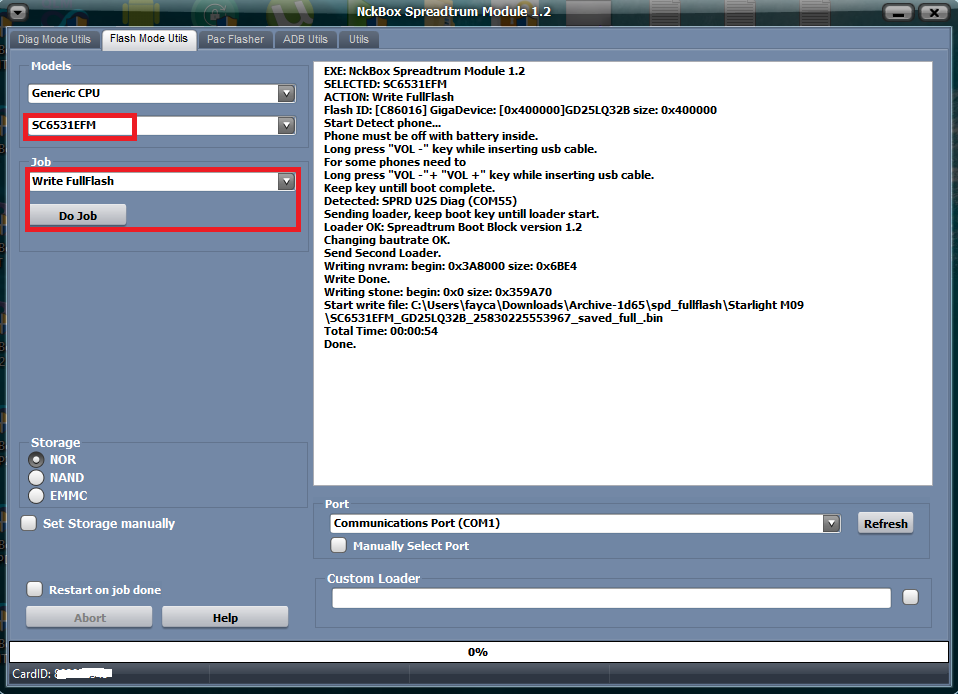
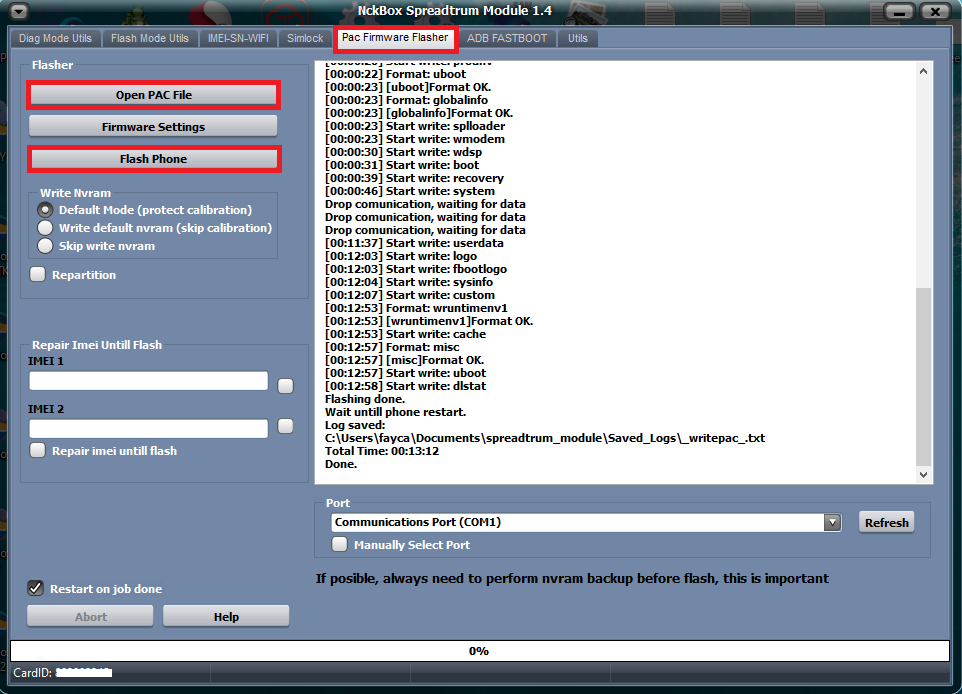
Huawei Y3C (Y336-U02) Flash Done
Huawei Y3C (Y336-U02) Flash Done

كود:
EXE: NckBox Spreadtrum Module 1.4ACTION: Flash Firmware.
Selected firmware: Y336-U02V100R001C328B109.pac
NV: Default Mode (protect calibration)
Device Storage: EMMC
Detected: SPRD U2S Diag (COM6)
[00:00:00] Sending loader.
BOOT: ~SPRD3W
~
Sending loader, keep boot key untill loader start.
[00:00:03] Loader ok
[00:00:03] Reconnecting .
Detected: SPRD U2S Diag (COM6)
[00:00:05] Wait for loader....
Loader OK: ~"Spreadtrum Boot Block version 1.1
Changing bautrate OK.
[00:00:05] First boot done.
[00:00:05] Sending second loader.
[00:00:09] Second loader sent ok.
[00:00:09] Reading: miscdata
[00:00:09] Reading: wfixnv1
NVRAM saved to: C:\Users\fayca\Documents\spreadtrum_module\spd_nvram_backup\_862906038214461\_862906038214461_nvram_backup.tar
[00:00:18] Start write: wfixnv1
Protecting GSM_CALI_ITEM_ID id: 0x2
Protecting W_Calibration id: 0x12D
Protecting BlueTooth id: 0x191
Protecting BandSelect id: 0xD
Protecting WIFI id: 0x199
Protecting MMITest id: 0x19A
Protecting SimLockSign id: 0x19F
Protecting SupportGsmOnly id: 0x7E4
Protecting SimLockCustomize id: 0x1F0
Protecting SimLockUserdata id: 0x1F1
Protecting SimLockCtrlkey id: 0x1F2
[00:00:20] Format: dlstat
[00:00:20] [dlstat]Format OK.
[00:00:20] Start write: prodnv
[00:00:22] Format: uboot
[00:00:23] [uboot]Format OK.
[00:00:23] Format: globalinfo
[00:00:23] [globalinfo]Format OK.
[00:00:23] Start write: splloader
[00:00:23] Start write: wmodem
[00:00:30] Start write: wdsp
[00:00:31] Start write: boot
[00:00:39] Start write: recovery
[00:00:46] Start write: system
Drop comunication, waiting for data
Drop comunication, waiting for data
Drop comunication, waiting for data
[00:11:37] Start write: userdata
[00:12:03] Start write: logo
[00:12:03] Start write: fbootlogo
[00:12:04] Start write: sysinfo
[00:12:07] Start write: custom
[00:12:53] Format: wruntimenv1
[00:12:53] [wruntimenv1]Format OK.
[00:12:53] Start write: cache
[00:12:57] Format: misc
[00:12:57] [misc]Format OK.
[00:12:57] Start write: uboot
[00:12:58] Start write: dlstat
Flashing done.
Wait untill phone restart.
Log saved:
C:\Users\fayca\Documents\spreadtrum_module\Saved_Logs\_writepac_.txt
Total Time: 00:13:12
Done.- إنضم
- 16 سبتمبر 2012
- المشاركات
- 3,595
- مستوى التفاعل
- 3,276
- النقاط
- 113
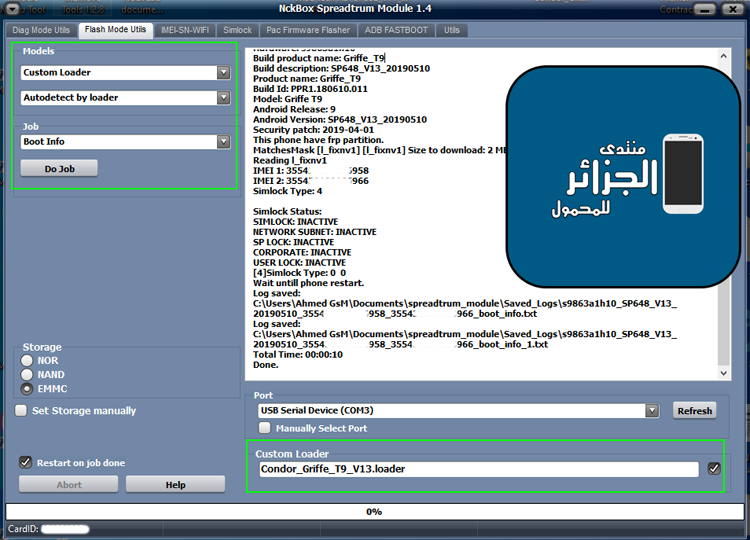
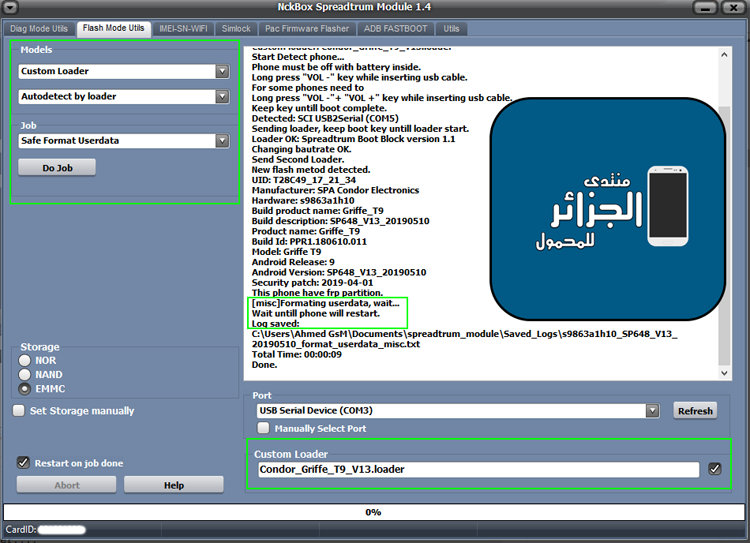
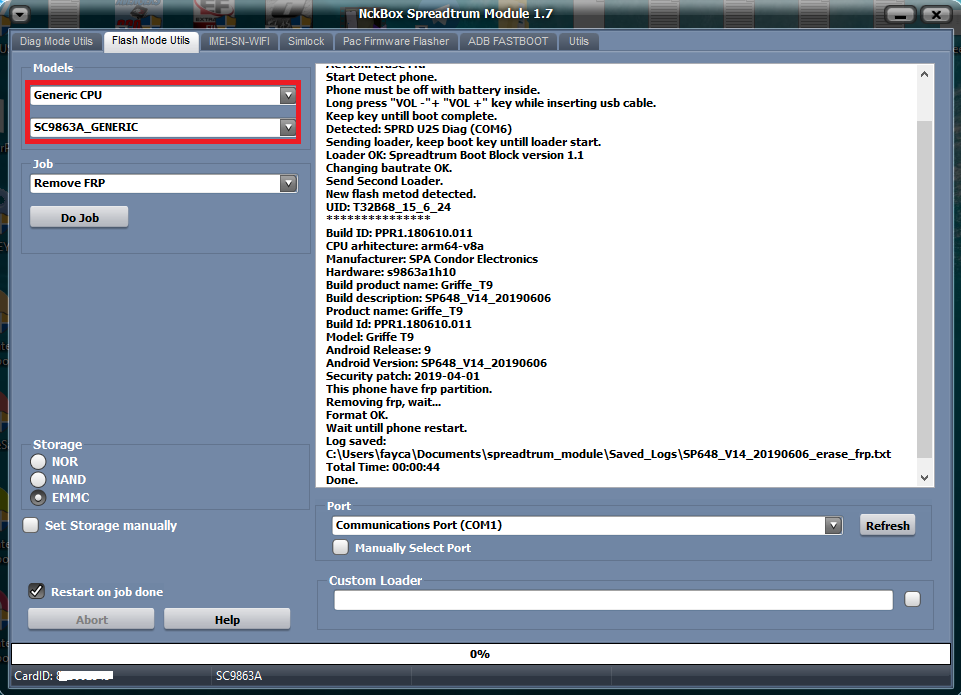
Condor Griffe T9 (SP648) FRP Reset
Condor Griffe T9 (SP648) FRP Reset

كود:
[/B][/SIZE]Phone Storage: EMMC[/CENTER]
EXE: NckBox Spreadtrum Module 1.7
SELECTED: SC9863A_GENERIC
ACTION: Erase FRP
Start Detect phone.
Phone must be off with battery inside.
Long press "VOL -"+ "VOL +" key while inserting usb cable.
Keep key untill boot complete.
Detected: SPRD U2S Diag (COM6)
Sending loader, keep boot key untill loader start.
Loader OK: Spreadtrum Boot Block version 1.1
Changing bautrate OK.
Send Second Loader.
New flash metod detected.
UID: T32B68_15_6_24
***************
Build ID: PPR1.180610.011
CPU arhitecture: arm64-v8a
Manufacturer: SPA Condor Electronics
Hardware: s9863a1h10
Build product name: Griffe_T9
Build description: SP648_V14_20190606
Product name: Griffe_T9
Build Id: PPR1.180610.011
Model: Griffe T9
Android Release: 9
Android Version: SP648_V14_20190606
Security patch: 2019-04-01
This phone have frp partition.
Removing frp, wait...
Format OK.
Wait untill phone restart.
Log saved:
C:\Users\fayca\Documents\spreadtrum_module\Saved_Logs\SP648_V14_20190606_erase_frp.txt
Total Time: 00:00:44
[CENTER]Done.[SIZE=6][B]- إنضم
- 16 سبتمبر 2012
- المشاركات
- 3,595
- مستوى التفاعل
- 3,276
- النقاط
- 113
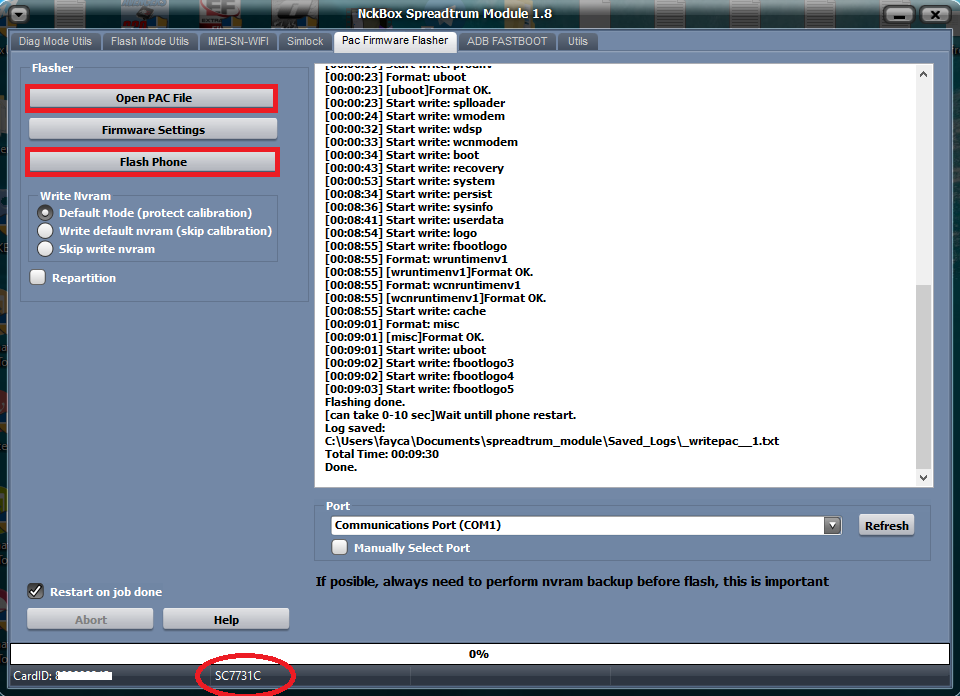
Kiowa X4 Flash done
Kiowa X4 Flash done

كود:
EXE: NckBox Spreadtrum Module 1.8ACTION: Flash Firmware.
Selected firmware: KIOWA_X4_V003_20170601.pac
NV: Default Mode (protect calibration)
Device Storage: EMMC
Start Detect phone.
Phone must be off with battery inside.
Long press "VOL -" key while inserting usb cable.
Keep key untill boot complete.
Detected: SPRD U2S Diag (COM6)
[00:00:00] Sending loader.
BOOT: SPRD3
Sending loader, keep boot key untill loader start.
[00:00:02] Loader ok
[00:00:02] Wait for loader....
Loader OK: ~"Spreadtrum Boot Block version 1.1
Changing bautrate OK.
[00:00:03] First boot done.
[00:00:03] Sending second loader.
[00:00:08] Second loader sent ok.
[00:00:08] Reading: miscdata
[00:00:08] Reading: wfixnv1
NVRAM saved to: C:\Users\fayca\Documents\spreadtrum_module\flashmode_nvram_backup\_353222078134676\_353222078134676_nvram_backup.tar
[00:00:17] Start write: wfixnv1
Protecting GSM_CALI_ITEM_ID id: 0x2
Protecting W_Calibration id: 0x12D
Protecting BlueTooth id: 0x191
Protecting BandSelect id: 0xD
Protecting WIFI id: 0x199
Protecting MMITest id: 0x19A
Protecting WIFICal1 id: 0x19F
Protecting WIFICal2 id: 0x1A0
Protecting WIFICal3 id: 0x1A1
[00:00:19] Start write: wcnfixnv1
[00:00:19] Start write: prodnv
[00:00:23] Format: uboot
[00:00:23] [uboot]Format OK.
[00:00:23] Start write: splloader
[00:00:24] Start write: wmodem
[00:00:32] Start write: wdsp
[00:00:33] Start write: wcnmodem
[00:00:34] Start write: boot
[00:00:43] Start write: recovery
[00:00:53] Start write: system
[00:08:34] Start write: persist
[00:08:36] Start write: sysinfo
[00:08:41] Start write: userdata
[00:08:54] Start write: logo
[00:08:55] Start write: fbootlogo
[00:08:55] Format: wruntimenv1
[00:08:55] [wruntimenv1]Format OK.
[00:08:55] Format: wcnruntimenv1
[00:08:55] [wcnruntimenv1]Format OK.
[00:08:55] Start write: cache
[00:09:01] Format: misc
[00:09:01] [misc]Format OK.
[00:09:01] Start write: uboot
[00:09:02] Start write: fbootlogo3
[00:09:02] Start write: fbootlogo4
[00:09:03] Start write: fbootlogo5
Flashing done.
[can take 0-10 sec]Wait untill phone restart.
Log saved:
C:\Users\fayca\Documents\spreadtrum_module\Saved_Logs\_writepac__1.txt
Total Time: 00:09:30
Done.- إنضم
- 16 سبتمبر 2012
- المشاركات
- 3,595
- مستوى التفاعل
- 3,276
- النقاط
- 113
Condor Plume L4 SP642 FRP Reset
Condor Plume L4 SP642 FRP Reset
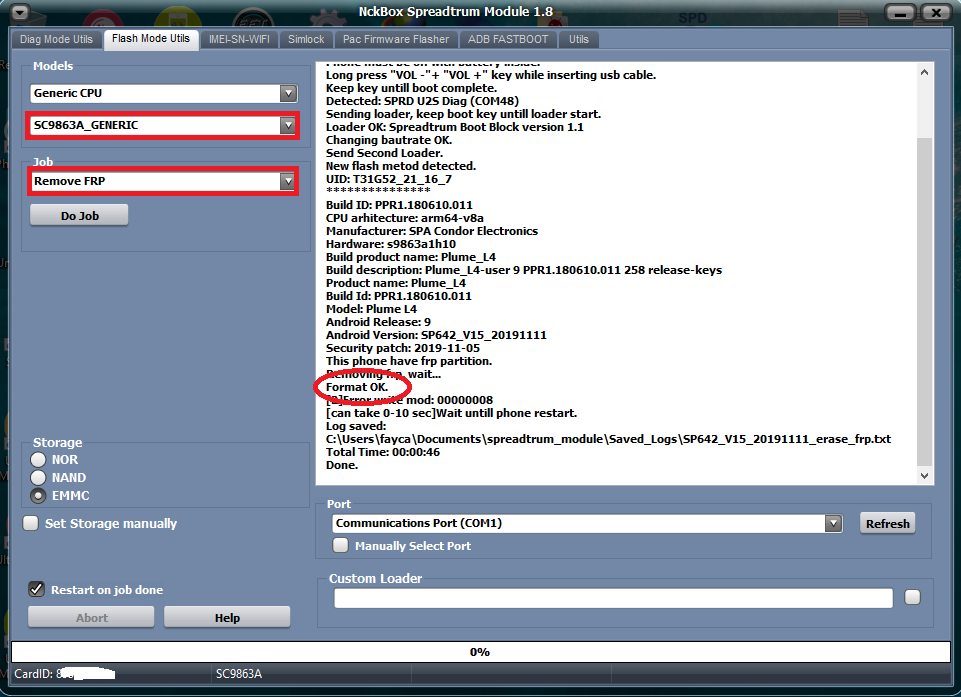

كود:
Phone Storage: EMMCEXE: NckBox Spreadtrum Module 1.8
SELECTED: [COLOR=#ff0000]SC9863A_GENERIC[/COLOR]
ACTION: Erase FRP
Start Detect phone.
Phone must be off with battery inside.
Long press "VOL -"+ "VOL +" key while inserting usb cable.
Keep key untill boot complete.
Detected: SPRD U2S Diag (COM48)
Sending loader, keep boot key untill loader start.
Loader OK: Spreadtrum Boot Block version 1.1
Changing bautrate OK.
Send Second Loader.
New flash metod detected.
UID: T31G52_21_16_7
***************
Build ID: PPR1.180610.011
CPU arhitecture: arm64-v8a
Manufacturer: SPA Condor Electronics
Hardware: s9863a1h10
Build product name: Plume_L4
Build description: Plume_L4-user 9 PPR1.180610.011 258 release-keys
Product name: Plume_L4
Build Id: PPR1.180610.011
Model: [COLOR=#ff0000]Plume L4[/COLOR]
Android Release: 9
Android Version: SP642_V15_20191111
Security patch: 2019-11-05
This phone have frp partition.
Removing frp, wait...
[COLOR=#ff0000]Format OK[/COLOR].
[2]Error write mod: 00000008
[can take 0-10 sec]Wait untill phone restart.
Log saved:
C:\Users\fayca\Documents\spreadtrum_module\Saved_Logs\SP642_V15_20191111_erase_frp.txt
Total Time: 00:00:46
Done.رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
Starlight M05 User Code Reset
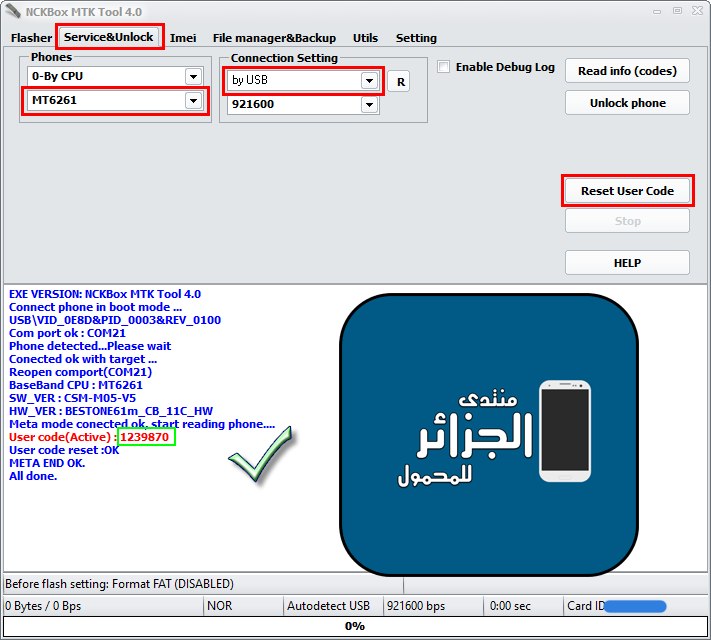
Starlight M05 User Code Reset

كود:
[B][FONT=Arial Black][SIZE=2] EXE VERSION: NCKBox MTK Tool 4.0
Connect phone in boot mode ...
USB\VID_0E8D&PID_0003&REV_0100
Com port ok : COM21
Phone detected...Please wait
Conected ok with target ...
Reopen comport(COM21)
BaseBand CPU : MT6261
SW_VER : CSM-M05-V5
HW_VER : BESTONE61m_CB_11C_HW
Meta mode conected ok, start reading phone....
[COLOR="#FF0000"] User code(Active) : 1239870
[/COLOR] User code reset :OK
META END OK.
All done.[/SIZE][/FONT]
[/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
فك شفرة Alcatel OT-506
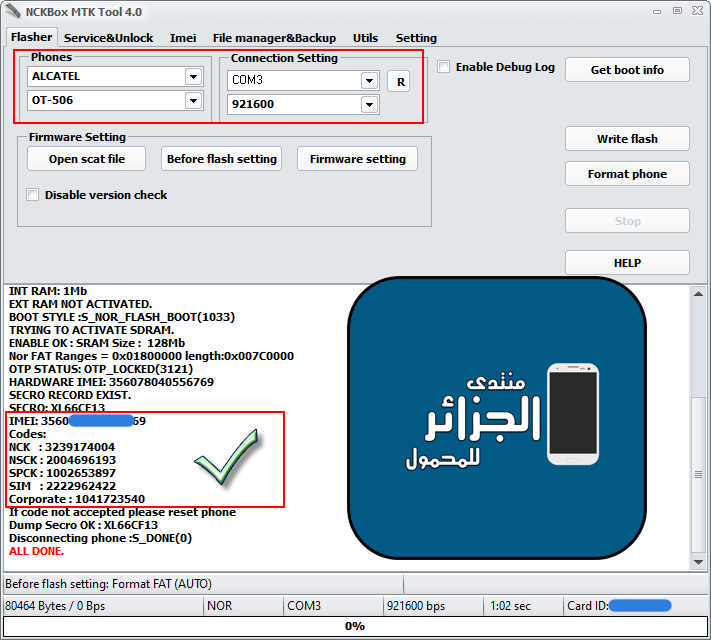
فك شفرة Alcatel OT-506

كود:
[B][FONT=Arial Black][SIZE=2] EXE VERSION: NCKBox MTK Tool 4.0
DA version: 5.1428.00.00
USER SELECTION : BOOT INFO.
MODEL SELECTED : OT-506
PHONE MUST BE OFF WITH BATTERY INSIDE.
Com port opened...Press power on
Download DA now...You can release power on
CHANGE BAUDRATE SUCCES :S_DONE(0)
DA download finished...Getting phone info
BaseBand CPU: MT6253_S00
BaseBand CPU Secure Version : 3 (Secure baseband)
FLASH TYPE : NOR
ID: NOR:(256Mb+0Kb) [SPANSION] S25FL032P size:0x02000000
INT RAM: 1Mb
EXT RAM NOT ACTIVATED.
BOOT STYLE :S_NOR_FLASH_BOOT(1033)
TRYING TO ACTIVATE SDRAM.
ENABLE OK : SRAM Size : 128Mb
Nor FAT Ranges = 0x01800000 length:0x007C0000
OTP STATUS: OTP_LOCKED(3121)
HARDWARE IMEI: 356078040556769
SECRO RECORD EXIST.
SECRO: XL66CF13
IMEI: 35607XXXXXXX69
[COLOR="#FF0000"] Codes:
NCK : 3239174004
NSCK : 2004696193
SPCK : 1002653897
SIM : 2222962422
Corporate : 1041723540
[/COLOR] If code not accepted please reset phone
Dump Secro OK : XL66CF13
Disconnecting phone :S_DONE(0)
ALL DONE.
[/SIZE][/FONT][/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
STREAM B1s Flash Done
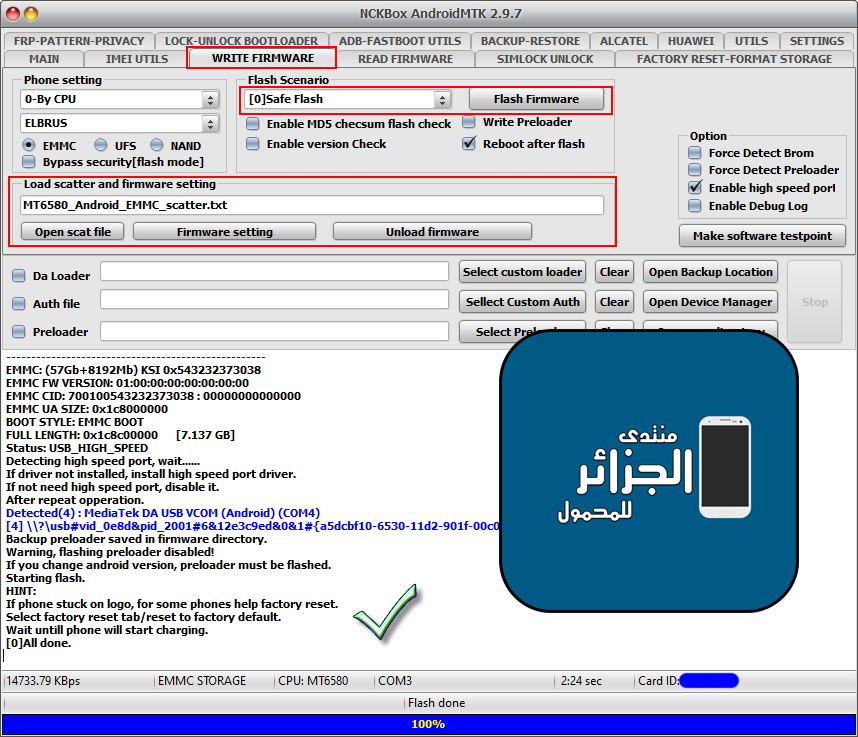
STREAM B1s Flash Done

كود:
[B][FONT=Arial Black][SIZE=2] Flash files count is :16
Action : Firmware update.
Selected Model: 0-By CPU: ELBRUS
Exe version: NCKBox AndroidMTK 2.9.7
Scenario: [0]Safe Flash
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(3) : MediaTek PreLoader USB VCOM (Android) (COM3)
[3] \\?\usb#vid_0e8d&pid_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Preloader
BBCHIP: 6580 0 ca00
Using Algo 1.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6580
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 1 GB DRAM
----------------------------------------------------
EMMC: (57Gb+8192Mb) KSI 0x543232373038
EMMC FW VERSION: 01:00:00:00:00:00:00:00
EMMC CID: 700100543232373038 : 00000000000000
EMMC UA SIZE: 0x1c8000000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x1c8c00000 [7.137 GB]
Status: USB_HIGH_SPEED
Detecting high speed port, wait......
If driver not installed, install high speed port driver.
If not need high speed port, disable it.
After repeat opperation.
Detected(4) : MediaTek DA USB VCOM (Android) (COM4)
[4] \\?\usb#vid_0e8d&pid_2001#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Backup preloader saved in firmware directory.
Warning, flashing preloader disabled!
If you change android version, preloader must be flashed.
Starting flash.
HINT:
If phone stuck on logo, for some phones help factory reset.
Select factory reset tab/reset to factory default.
Wait untill phone will start charging.
[0]All done.
[/SIZE][/FONT][/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
LG K4 2017 (X230ds) Reset To Factory + Reset FRP
تبويت الجهاز بزر خفض الصوت -
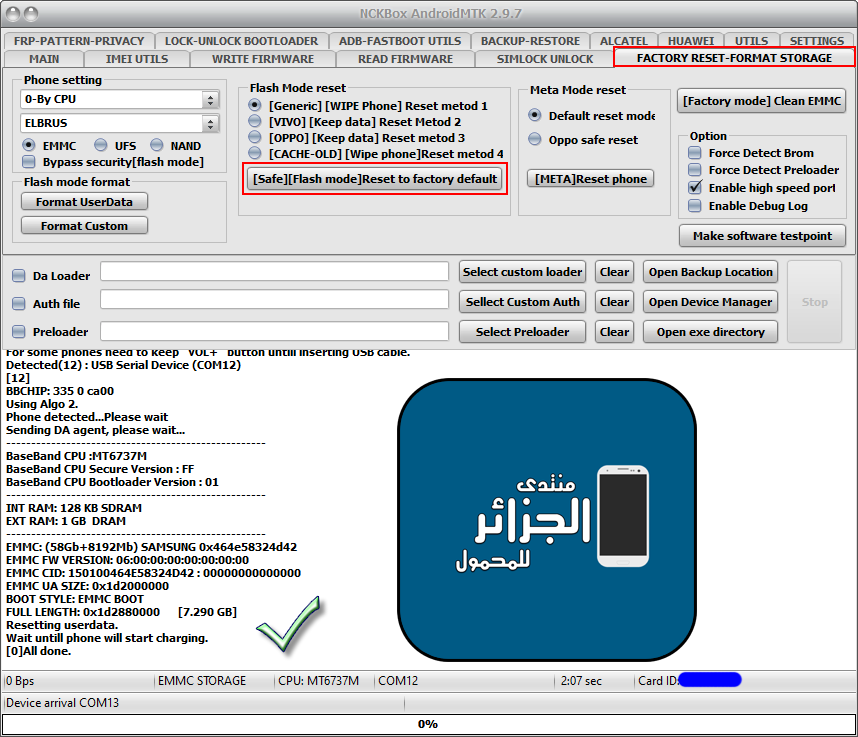
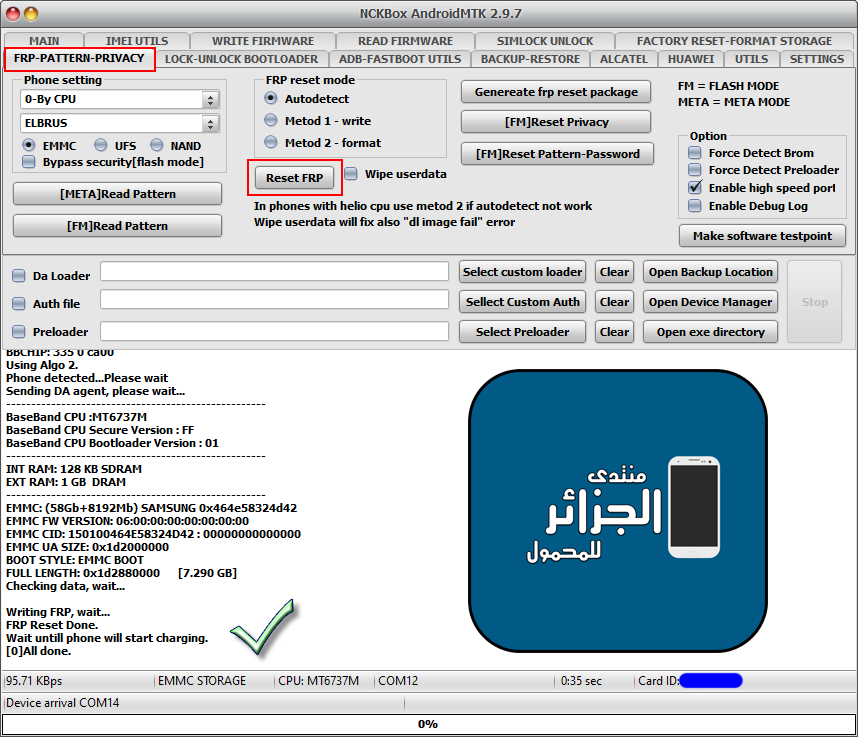
LG K4 2017 (X230ds) Reset To Factory + Reset FRP
تبويت الجهاز بزر خفض الصوت -

كود:
[B][FONT=Arial Black][SIZE=2] [MISC]Action: Reset To Factory.
Selected 0-By CPU:ELBRUS
Exe version: NCKBox AndroidMTK 2.9.7
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(12) : USB Serial Device (COM12)
[12]
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6737M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 1 GB DRAM
----------------------------------------------------
EMMC: (58Gb+8192Mb) SAMSUNG 0x464e58324d42
EMMC FW VERSION: 06:00:00:00:00:00:00:00
EMMC CID: 150100464E58324D42 : 00000000000000
EMMC UA SIZE: 0x1d2000000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x1d2880000 [7.290 GB]
Resetting userdata.
Wait untill phone will start charging.
[0]All done.
[/SIZE][/FONT][/B]
كود:
[B][FONT=Arial Black][SIZE=2] Exe version: NCKBox AndroidMTK 2.9.7
Selected model: 0-By CPU ELBRUS
[auto]Action: Reset FRP
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(12) : USB Serial Device (COM12)
[12]
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6737M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 1 GB DRAM
----------------------------------------------------
EMMC: (58Gb+8192Mb) SAMSUNG 0x464e58324d42
EMMC FW VERSION: 06:00:00:00:00:00:00:00
EMMC CID: 150100464E58324D42 : 00000000000000
EMMC UA SIZE: 0x1d2000000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x1d2880000 [7.290 GB]
Checking data, wait...
Writing FRP, wait...
FRP Reset Done.
Wait untill phone will start charging.
[0]All done.
[/SIZE][/FONT][/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
Starlight Future FRP Reset Done
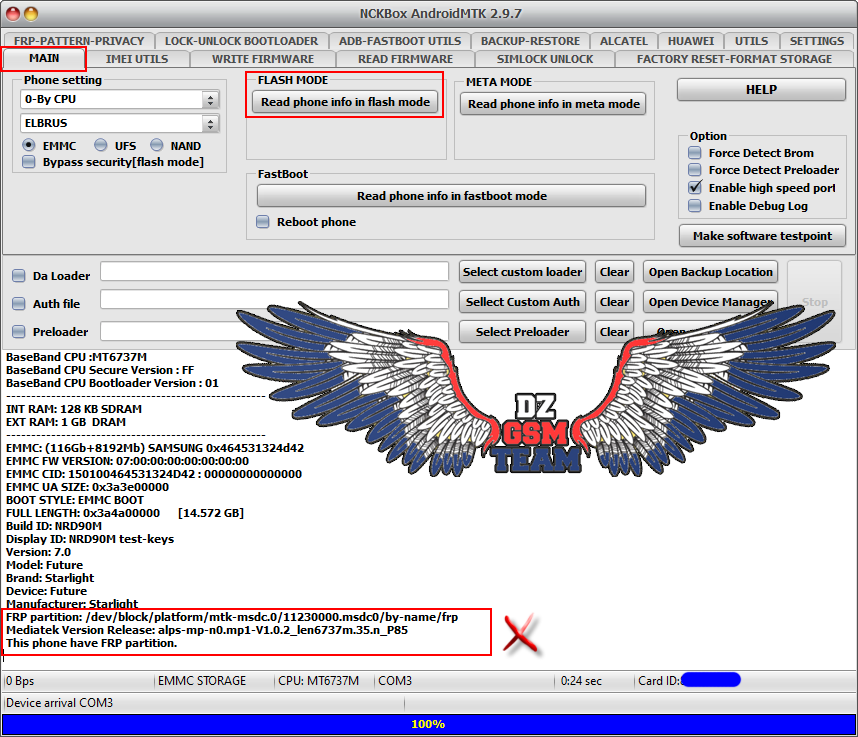
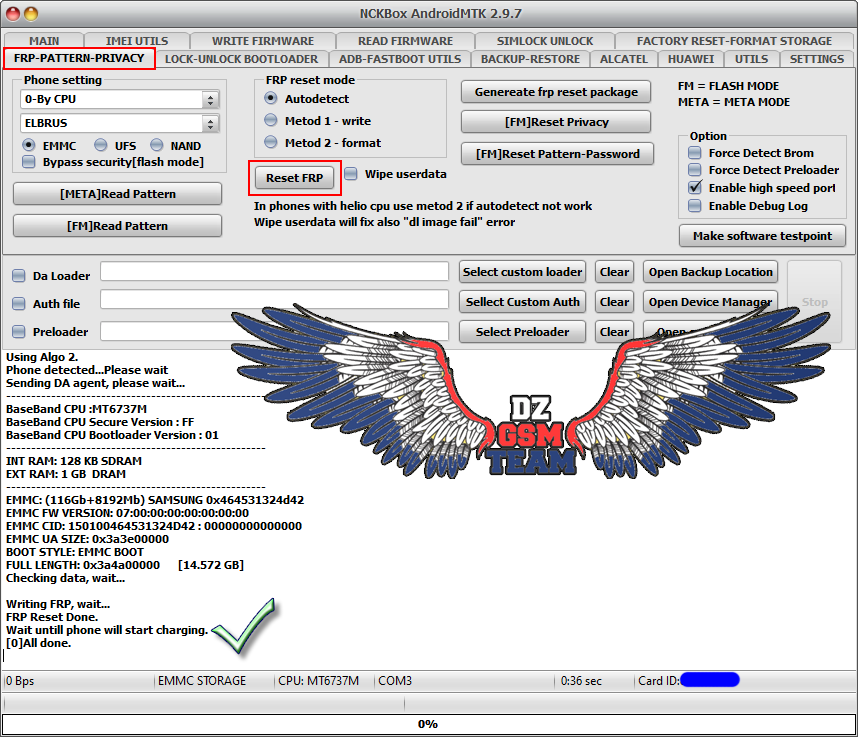
Starlight Future FRP Reset Done


كود:
[B][FONT=Arial Black][SIZE=2] Exe version: NCKBox AndroidMTK 2.9.7
Selected model: 0-By CPU ELBRUS
[auto]Action: Reset FRP
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(3) : MediaTek PreLoader USB VCOM (Android) (COM3)
[3] \\?\usb#vid_0e8d&pid_2000#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Preloader
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6737M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 1 GB DRAM
----------------------------------------------------
EMMC: (116Gb+8192Mb) SAMSUNG 0x464531324d42
EMMC FW VERSION: 07:00:00:00:00:00:00:00
EMMC CID: 150100464531324D42 : 00000000000000
EMMC UA SIZE: 0x3a3e00000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x3a4a00000 [14.572 GB]
Checking data, wait...
Writing FRP, wait...
FRP Reset Done.
Wait untill phone will start charging.
[0]All done.
[/SIZE][/FONT][/B]رد: تجارب الاعضاء فى تفليش وعمل ريبير وفك الشفرة على NckBox
Xiaomi Redmi 9A (dandelion) Unlocking bootloader Done
NckBox MTK
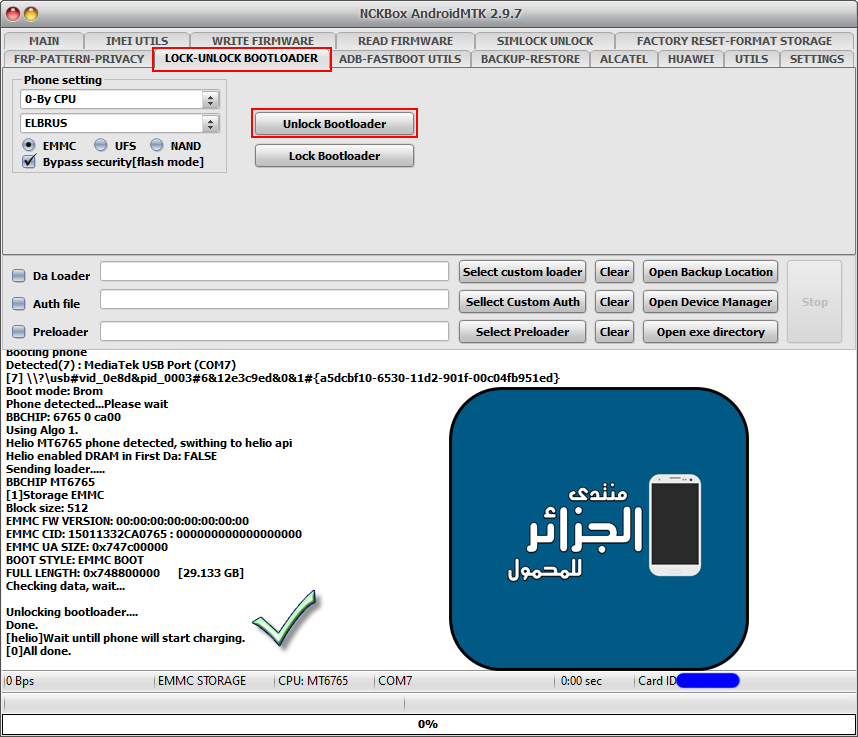
Xiaomi Redmi 9A (dandelion) Unlocking bootloader Done
NckBox MTK

كود:
[B][FONT=Arial Black][SIZE=2] Exe version: NCKBox AndroidMTK 2.9.7
Selected model: 0-By CPU ELBRUS
Action: [COLOR="#FF0000"]Unlock Bootloader[/COLOR]
Phone must be off with battery inside.
Battery must be charged
Please connect phone in brom mode
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(7) : MediaTek USB Port (COM7)
[7] \\?\usb#vid_0e8d&pid_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
CPU: MT6765 CPU code: 766 Target config: e7
***********************
Secure boot enabled: true
Need serial link authorization: true
Need download agent authorization: true
SWJTAG enabled: true
EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: false
Root cert required: false
Memory read authorization: true
Memory write authorization: true
Cmd 0xC8 blocked: true
***********************
Executing exploit, do not disconnect phone
Exploit has been executed successfully.
[3ac00]Dumping phone preloader.
Preloader: C:\ProgramData\Android_MTK_Backup_Folder\preloader_backup\preloader_k62v1_64_bsp.bin
Waiting for handle to become active......
Reseived active handle repply from phone......
Booting phone
Detected(7) : MediaTek USB Port (COM7)
[7] \\?\usb#vid_0e8d&pid_0003#6&12e3c9ed&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Brom
Phone detected...Please wait
BBCHIP: 6765 0 ca00
Using Algo 1.
Helio MT6765 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6765
[1]Storage EMMC
Block size: 512
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 15011332CA0765 : 000000000000000000
EMMC UA SIZE: 0x747c00000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x748800000 [29.133 GB]
Checking data, wait...
[COLOR="#FF0000"] Unlocking bootloader....
Done.
[/COLOR] [helio]Wait untill phone will start charging.
[0]All done.
[/SIZE][/FONT][/B]