- إنضم
- 6 يونيو 2016
- المشاركات
- 359
- مستوى التفاعل
- 525
- النقاط
- 93

تخطي حساب جوجل للهاتف العنيد Huawei Y3 2017 CRO L22
تم التخطي بنجاح على العملاق EFT Dongle وباضافة ملف Secure Boot DA File
================
لوج بيانات الهاتف
كود:
[LEFT]Wating Device..........OK
CPU: MT6737M
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 1.00 GB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 512.00 KB
EMMC PART USER Size: 7.28 GB
Battery:
Battery Voltage: 3845
Injection..........OK
Detecting Parts info............OK
[ID: 8] [proinfo] BaseAddr(0x00080000) Size(0x00300000)
[ID: 8] [nvram] BaseAddr(0x00380000) Size(0x00500000)
[ID: 8] [protect1] BaseAddr(0x00880000) Size(0x00a00000)
[ID: 8] [protect2] BaseAddr(0x01280000) Size(0x00a00000)
[ID: 8] [lk] BaseAddr(0x01c80000) Size(0x00080000)
[ID: 8] [para] BaseAddr(0x01d00000) Size(0x00080000)
[ID: 8] [boot] BaseAddr(0x01d80000) Size(0x01000000)
[ID: 8] [recovery] BaseAddr(0x02d80000) Size(0x01000000)
[ID: 8] [logo] BaseAddr(0x03d80000) Size(0x00800000)
[ID: 8] [expdb] BaseAddr(0x04580000) Size(0x00a00000)
[ID: 8] [seccfg] BaseAddr(0x04f80000) Size(0x00080000)
[ID: 8] [oemkeystore] BaseAddr(0x05000000) Size(0x00200000)
[ID: 8] [secro] BaseAddr(0x05200000) Size(0x00600000)
[ID: 8] [keystore] BaseAddr(0x05800000) Size(0x00800000)
[ID: 8] [tee1] BaseAddr(0x06000000) Size(0x00500000)
[ID: 8] [tee2] BaseAddr(0x06500000) Size(0x00500000)
[ID: 8] [bak] BaseAddr(0x06a00000) Size(0x00800000)
[ID: 8] [bakraw] BaseAddr(0x07200000) Size(0x00200000)
[ID: 8] [simlock] BaseAddr(0x07400000) Size(0x00800000)
[ID: 8] [custom] BaseAddr(0x07c00000) Size(0x0c800000)
[ID: 8] [frp] BaseAddr(0x14400000) Size(0x00100000)
[ID: 8] [nvdata] BaseAddr(0x14500000) Size(0x02000000)
[ID: 8] [metadata] BaseAddr(0x16500000) Size(0x02300000)
[ID: 8] [system] BaseAddr(0x18800000) Size(0x9c800000)
[ID: 8] [cache] BaseAddr(0xb5000000) Size(0x0f000000)
[ID: 8] [userdata] BaseAddr(0xc4000000) Size(0x10cf80000)
[ID: 8] [flashinfo] BaseAddr(0x1d0f80000) Size(0x01000000)
Detecting Device info.......OK
Product: HUAWEI
[COLOR="#FF0000"]Device Model: CRO-L22
ID: Cairo-L22C185B127[/COLOR]
Sw Internal:
Build Date: Fri Jun 22 20:53:18 CST 2018
Chip Ver: S01
Android Version: 6.0
Architecture: armeabi-v7a
[/LEFT]All Done By EFT Dongle=============================
لوج عملية التخطي
كود:
[LEFT]Wating Device..........OK
CPU: MT6737M
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 1.00 GB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 512.00 KB
EMMC PART USER Size: 7.28 GB
Battery:
Battery Voltage: 3837
Injection..........OK
Detecting Parts info............OK
[ID: 8] [proinfo] BaseAddr(0x00080000) Size(0x00300000)
[ID: 8] [nvram] BaseAddr(0x00380000) Size(0x00500000)
[ID: 8] [protect1] BaseAddr(0x00880000) Size(0x00a00000)
[ID: 8] [protect2] BaseAddr(0x01280000) Size(0x00a00000)
[ID: 8] [lk] BaseAddr(0x01c80000) Size(0x00080000)
[ID: 8] [para] BaseAddr(0x01d00000) Size(0x00080000)
[ID: 8] [boot] BaseAddr(0x01d80000) Size(0x01000000)
[ID: 8] [recovery] BaseAddr(0x02d80000) Size(0x01000000)
[ID: 8] [logo] BaseAddr(0x03d80000) Size(0x00800000)
[ID: 8] [expdb] BaseAddr(0x04580000) Size(0x00a00000)
[ID: 8] [seccfg] BaseAddr(0x04f80000) Size(0x00080000)
[ID: 8] [oemkeystore] BaseAddr(0x05000000) Size(0x00200000)
[ID: 8] [secro] BaseAddr(0x05200000) Size(0x00600000)
[ID: 8] [keystore] BaseAddr(0x05800000) Size(0x00800000)
[ID: 8] [tee1] BaseAddr(0x06000000) Size(0x00500000)
[ID: 8] [tee2] BaseAddr(0x06500000) Size(0x00500000)
[ID: 8] [bak] BaseAddr(0x06a00000) Size(0x00800000)
[ID: 8] [bakraw] BaseAddr(0x07200000) Size(0x00200000)
[ID: 8] [simlock] BaseAddr(0x07400000) Size(0x00800000)
[ID: 8] [custom] BaseAddr(0x07c00000) Size(0x0c800000)
[ID: 8] [frp] BaseAddr(0x14400000) Size(0x00100000)
[ID: 8] [nvdata] BaseAddr(0x14500000) Size(0x02000000)
[ID: 8] [metadata] BaseAddr(0x16500000) Size(0x02300000)
[ID: 8] [system] BaseAddr(0x18800000) Size(0x9c800000)
[ID: 8] [cache] BaseAddr(0xb5000000) Size(0x0f000000)
[ID: 8] [userdata] BaseAddr(0xc4000000) Size(0x10cf80000)
[ID: 8] [flashinfo] BaseAddr(0x1d0f80000) Size(0x01000000)
Detecting Device info.......OK
Product: HUAWEI
Device Model: CRO-L22
ID: Cairo-L22C185B127
Sw Internal:
Build Date: Fri Jun 22 20:53:18 CST 2018
Chip Ver: S01
Android Version: 6.0
Architecture: armeabi-v7a
[COLOR="#FF0000"]FRP RESET... [FRP] .....OK[/COLOR]
All Done By EFT Dongle[/LEFT]===========================
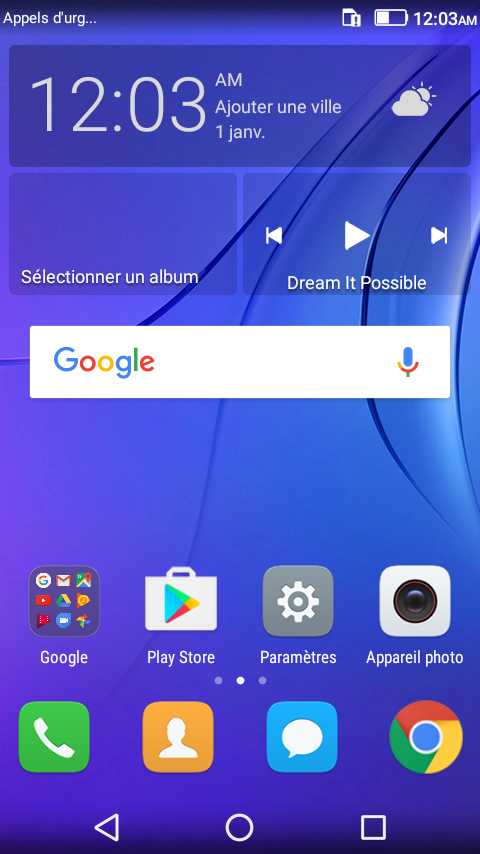
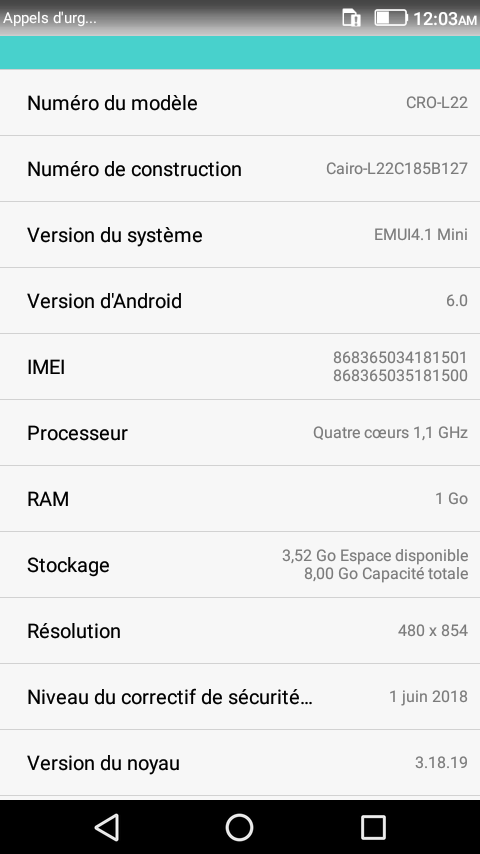
============================
تحميل ملف Secure Boot DA File
